When convicted Iranian sanctions evader Babak Zanjani claimed he sold cryptocurrency to Iran’s Central Bank, publishing stamped letters with wallet addresses on December 21, 2025, Crystal Intelligence investigated the infrastructure behind his allegations.
We found the wallets, and what they reveal is a sophisticated sanctions evasion infrastructure operating at an institutional scale.
Between April and May 2025, two wallets matching Zanjani’s description moved $48.9 million in USDT with systematic precision: one routed funds through cross-chain bridges and to Tether-blacklisted wallets, while the other sent 51% directly to OFAC-sanctioned entities. Both received funds from 92-94% uncategorized origins, processed institutional volumes within 15-30 days, then distributed through high-risk infrastructure.
The infrastructure patterns expose three compliance blind spots that enabled $48.9 million to move through sanctions evasion channels undetected, vulnerabilities that extend far beyond Iran.
Zanjani’s allegations and what blockchain forensics reveal
In tweets posted December 29, 2025, Zanjani claimed he sold “a few million dollars’ worth of USDT” to Iran’s Central Bank through Informatics Services Company, a state-owned entity providing banking infrastructure. He published what he described as stamped Central Bank letters documenting the transactions-including cryptocurrency wallet addresses he claimed were controlled by Informatics Services Company on behalf of the Central Bank.

Above: Copies of the documents shared on Babak Zanjani’s X feed on Dec 21, 2025.
Informatics Services Company denied dealing in cryptocurrency. The Central Bank neither confirmed nor denied the allegations.
Zanjani also alleged that shortly after revealing the wallet addresses publicly, they appeared on Israel’s sanctions list – suggesting either internal security breaches or external intelligence collection targeting Central Bank operations.
Crystal identified two wallets matching Zanjani’s description, with transaction patterns, timing, and volumes consistent with his claims of institutional-scale operations during April and May 2025. For compliance purposes, what matters is how the infrastructure operated and the blind spots that enabled it to function.
What the blockchain shows
Crystal identified two wallets matching Zanjani’s description, with timing, volumes, and transaction patterns consistent with his claims of institutional-scale operations during April and May 2025.
Wallet 1: THwJSxR9qREsgEQjX1cpRw4Rw9WbmPSHVh
Volume: $28.5 million USDT
Timeframe: April-May 2025
Activity pattern: 15-30 days
Origin analysis:
- 92.4% from uncategorized sources
- 4.8% from licensed exchanges
- 2.7% from payment processors
Destination analysis:
- Crystal’s forensics show strong connections with blocklisted wallets, NBCTF sanctions, and Iranian VASPs
- Additional analysis indicates systematic routing through Bridgers (cross-chain bridge service) and to Tether-blacklisted wallets
- 100% of outbound funds went to high-risk infrastructure categories
This wallet received 70% of its funds from TWnCRk6z6KrwbuszhN6HUkdLRUh4yaVXBh, a wallet that did over 515 million USDT in transactions in less than 2 months between April 21 and June 15, 2025.
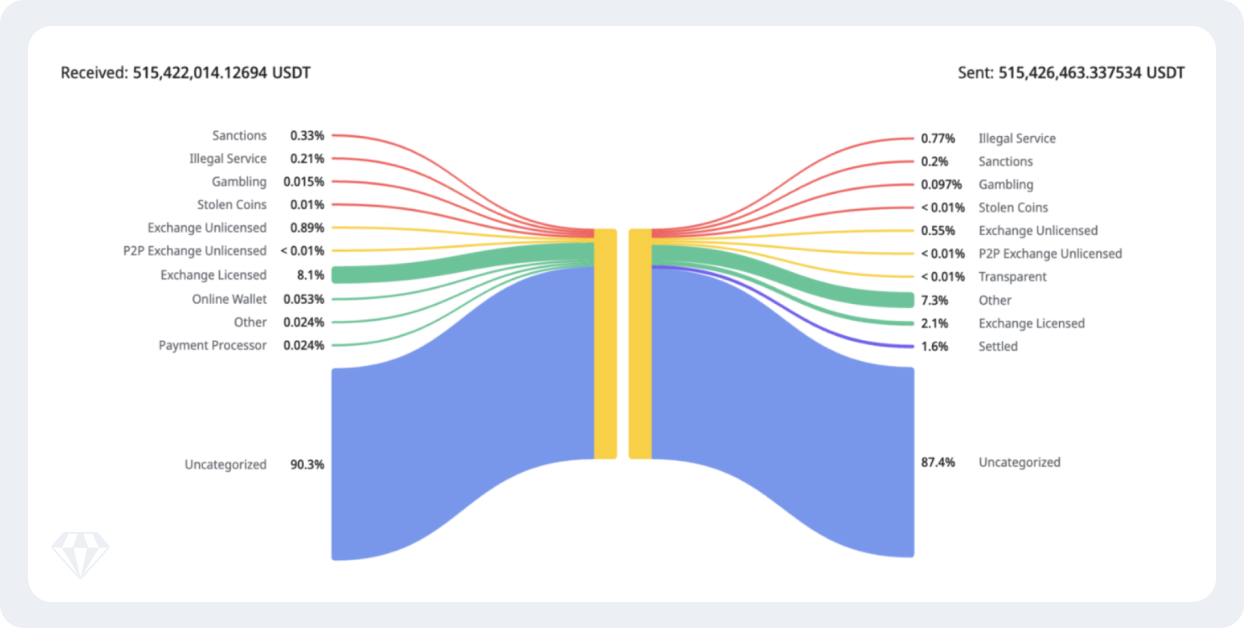
Above: A Crystal Export screenshot of source wallet TWnCR…aVXBh showing connections with high-risk entities
The above wallet shows strong connections with OFAC- and NBCTF-sanctioned entities linked to Iran and Russia, Iranian crypto exchanges, and also crypto cash desks located in Dubai, Hong Kong and Turkey.
Obfuscation of source and destination of funds
Our analysis of TRX gas fees for this wallet reveals that it received over 36% of TRX from an NBCTF-sanctioned wallet, providing further evidence that an Iran-linked entity controls the wallet. Furthermore, to obfuscate the on-chain trail, the wallet used two bridges in succession: first, converting USDT-TRX to USDT-ETH using Bridgers, and then converting the same to AEthUSDT using Aave.
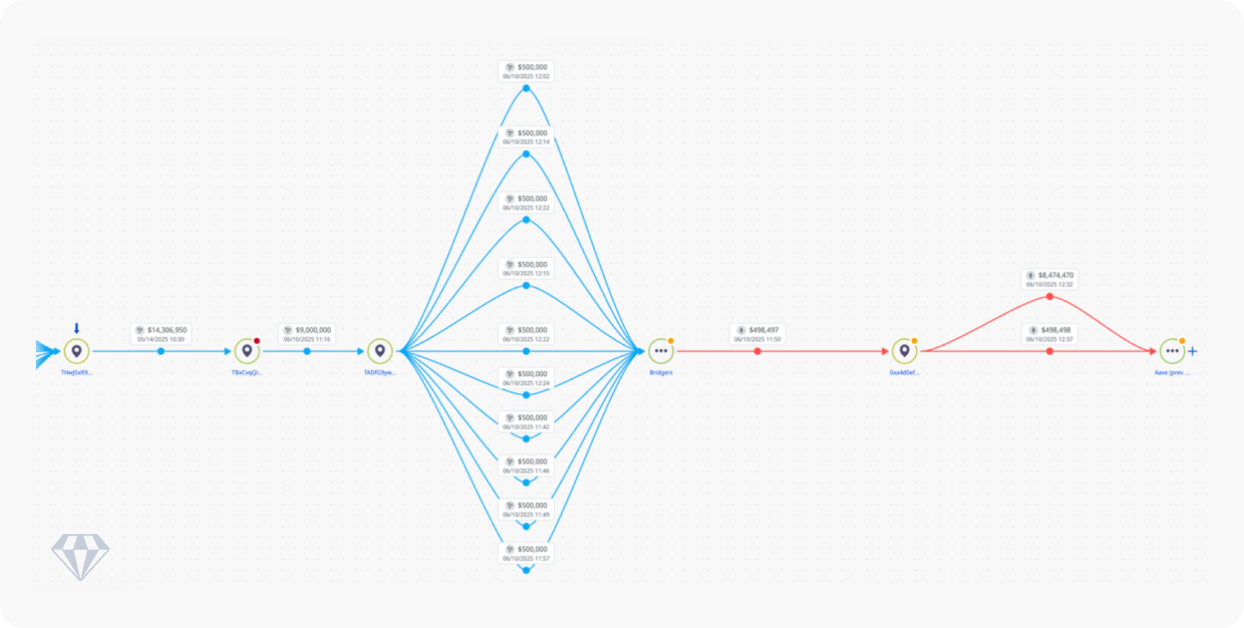
Above: Our analysis in Crystal Expert shows how the trail was obfuscated by converting the funds to ETH
Wallet 2: TBaxHwoXQjAmiNZgRKECoA3b6fsrtmoZvB
Volume: $20.6 million USDT
Timeframe: April-May 2025
Activity pattern: 15-30 days
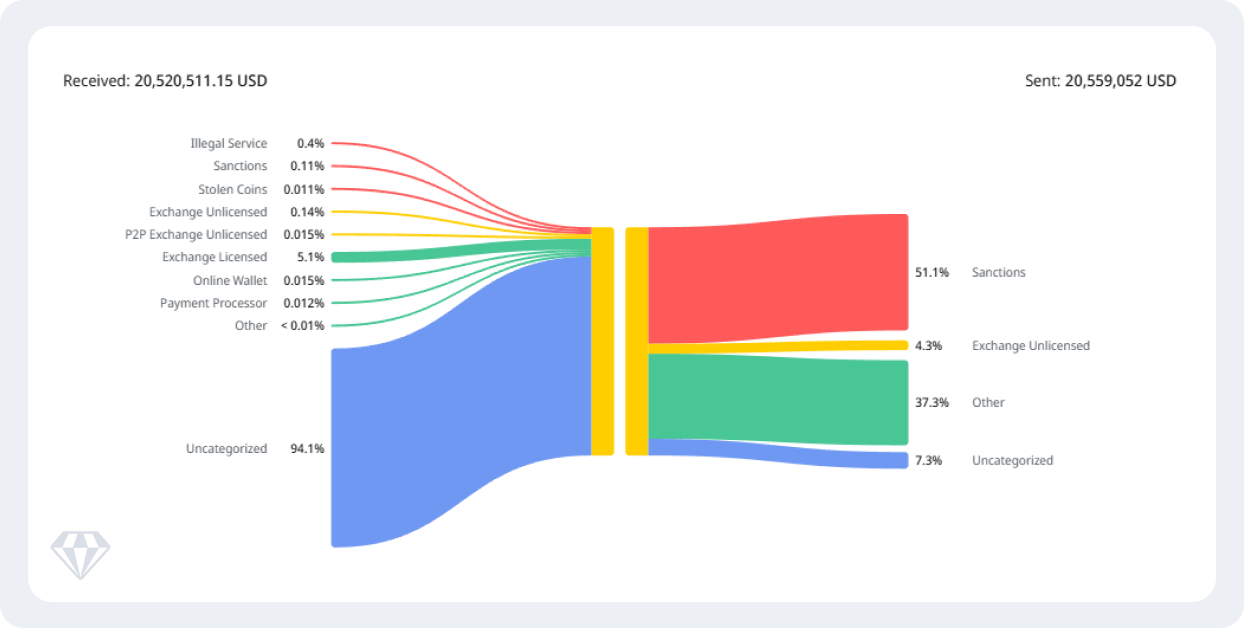
Above: Screenshot from Crystal Expert, illustrating the flows in an out of wallet TBaxHwoXQjAmiNZgRKECoA3b6fsrtmoZvB
Origin analysis:
- 94% from uncategorized sources
- Remaining 6% from mixed categories including illegal services (0.4%), sanctioned entities (0.11%), and licensed exchanges (5.3%)
Destination analysis:
- 51% sent to OFAC-sanctioned entities
- 37.3% to other categories (primarily Nobitex with IRGC-linked wallet connections, plus Bridgers and FixedFloat)
- 7.3% to uncategorized wallets
- 4.3% to unlicensed exchanges
The pattern across both wallets is consistent: funds arrive from largely untraceable origins, process through the wallet within concentrated timeframes, then distribute systematically to sanctions evasion infrastructure. Neither wallet shows mixed legitimate commerce – the transaction patterns indicate dedicated sanctions evasion operations.
Crystal’s origin wallet analysis shows patterns consistent with Garantex and A7A5 operators, both known sanctions evasion facilitators. The transaction volumes -$28.5M and $20.6M processed within 15-30 days – indicate institutional rather than retail scale, regardless of who controlled the operations.
Three compliance blind spots the infrastructure exploited
The wallet analysis reveals systematic vulnerabilities in sanctions compliance monitoring.
1. Cross-chain bridges sever compliance trails
The THwJS wallet shows systematic routing through cross-chain bridges alongside connections to Tether-blacklisted wallets. Crystal’s analysis reveals strong connections with blocklisted wallets, NBCTF sanctions, and Iranian VASPs, with infrastructure deliberately designed to break transaction history across blockchains.
Most compliance systems track activity within a single blockchain. When funds cross chains through bridge services, Virtual Asset Service Providers (VASPs) lose visibility into prior transaction history. The THwJS wallet exploited this gap: receive USDT with 92.4% origins uncategorized, then route through bridges to sever the chain, emerging on another blockchain with no visible connection to prior infrastructure.
The TBaxH wallet employed bridges alongside direct routing-37.3% of its funds went to categories including Bridgers and FixedFloat, while 51% went directly to OFAC-sanctioned entities. The combination demonstrates a sophisticated understanding of compliance vulnerabilities: some funds bridge across chains to break traceability, others route directly when the destination accepts the sanctions exposure.
For VASPs, the implication is clear: single-blockchain transaction monitoring cannot detect sanctions exposure that crosses chains. Without cross-chain tracing capabilities, compliance teams often see clean funds, whereas blockchain forensics reveals sanctioned origins.
2. Unlicensed exchanges operate outside compliance frameworks
The TBaxH wallet sent 51% of its $20.6 million directly to OFAC-sanctioned entities, with the majority of the funds routing through Nobitex-Iran’s largest cryptocurrency exchange, which has over 6 million users. OFAC sanctioned Nobitex in October 2024, but the exchange continues to operate, serving Iranian users who are unable to access international platforms due to restrictions. Crystal’s analysis shows these Nobitex flows included linked to IRGC wallets.
Unlicensed and unregistered exchanges create compliance blind spots because they operate entirely outside regulatory frameworks. They don’t implement KYC, don’t screen against sanctions lists, and don’t report suspicious activity. When funds move through these platforms, compliance teams at licensed VASPs see wallet addresses they cannot categorize.
The wallet patterns demonstrate how this gap enables institutional-scale sanctions evasion: funds arrive from 94% uncategorized origins at TBaxH, then 51% routes directly to sanctioned infrastructure through Nobitex. From a licensed VASP’s perspective monitoring only their own compliance perimeter, these transactions appear as movements to unidentified wallets rather than direct flows to OFAC-sanctioned entities and IRGC-linked infrastructure.
An additional 4.3% of TBaxH funds went to other unlicensed exchanges, reinforcing the pattern: systematic routing through platforms that operate beyond regulatory visibility.
3. Behavioral indicators go undetected without forensic context
Both wallets received funds from largely invisible origins: THwJS shows 92.4% from uncategorized sources, TBaxH shows 94%.
For compliance teams conducting standard screening, this presents as potentially legitimate activity, with funds arriving from unidentified wallets, which could be personal transfers, business payments, or any number of benign sources.
The compliance blind spot isn’t that destinations are unknown. Crystal’s analysis clearly categorized where funds went: systematic routing through bridges and to Tether-blacklisted wallets (THwJS); 51% to OFAC-sanctioned entities, 37.3% through Nobitex/bridges (TBaxH). The destinations are visible and high-risk.
The blind spot is that without behavioral analysis, high-risk destination patterns don’t trigger alerts:
- Volume concentration: $28.5M and $20.6M processed within 15-30 day windows – institutional-scale activity in compressed timeframes
- Systematic routing: The THwJS wallet shows 100% of outbound funds going to high-risk infrastructure categories. This isn’t mixed legitimate commerce with occasional high-risk transactions. This is dedicated sanctions evasion infrastructure.
- Destination clustering:TBaxH sent 51% directly to sanctioned entities, not as isolated transactions but as systematic operational pattern. When combined with 4.3% to unlicensed exchanges and 37.3% through Nobitex/IRGC-linked infrastructure, over 90% of outbound funds went to high-risk categories.
- Origin obscurity combined with high-risk destinations: Funds arrive from 92-94% uncategorized sources, then distribute with precision to sanctions evasion infrastructure. This pattern-untraceable origins, systematic high-risk routing, institutional volumes, compressed timeframes-indicates sophisticated operations at institutional scale.
- Infrastructure convergence: Both wallets connect to Garantex and A7A5 operator patterns in their origin analysis. These aren’t random wallet addresses engaging in occasional risky behavior. These are nodes within established sanctions evasion networks.
Static sanctions lists cannot detect these patterns. Wallets processing $28.5 million and $20.6 million from 92-94% uncategorized origins over 30 days, then routing systematically to high-risk infrastructure, demonstrate institutional-scale sanctions evasion even if the wallets themselves never appear on OFAC lists.
For compliance teams, this represents the evolution from list-based screening to behavioral analysis. The question shifts from “Is this wallet sanctioned?” to “Does this wallet’s transaction pattern-origin obscurity, volume concentration, systematic high-risk routing, infrastructure clustering-indicate sanctions evasion operations?”



