Crystal Intelligence hosted this webinar on cryptocurrency crime trends to educate and learn from law enforcement professionals, compliance officers, and financial institutions. Crystal’s VP of Training and Investigations at Crystal Intelligence, Nick Steegmans, moderated, joined by three experts:
- Andrew Fray, a forensic financial analyst with the US Secret Service’s Digital Assets Squad,
- Adam Zarazinski, CEO of Inca Digital, a Web3 risk intelligence firm, and
- Jonelle Still, Director of legal compliance, crypto, and AML/sanctions investigations at Mastercard’s Financial Intelligence Unit.
The session examined three critical typologies: address poisoning, risk washing, and Bitcoin ATM scams. Nick emphasized the timeliness of the discussion as law enforcement increasingly encounters cryptocurrency in investigations in the context of the industry adapting to new regulatory frameworks, such as the Guiding and Establishing National Innovation for U.S. Stablecoins Act (GENIUS Act) of July 2025.
Audience polls were also conducted during the webinar, with insightful results about how crypto crime is perpetrated, understood, and investigated.
To kick off, Poll 1 asked who had tuned in:

A healthy 41% of the audience were law enforcement agents and/or investigators, followed by 33% from the economic sector with direct concerns about crypto crime typologies.
To find out more, read on.
Understanding Address Poisoning
Poll 2 asked the audience what they knew about address poisoning:
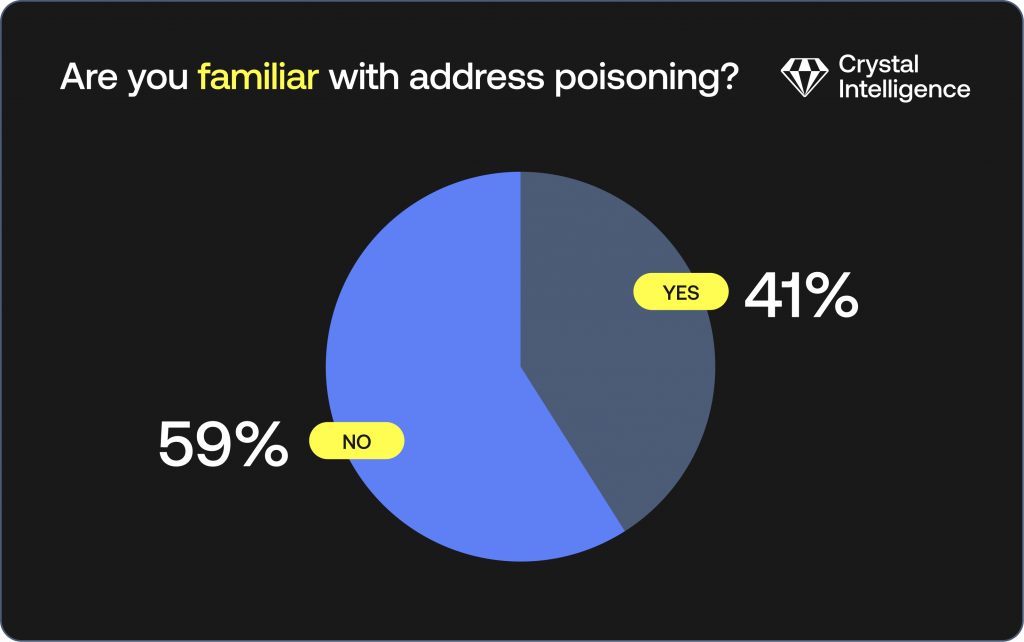
Despite Poll 1’s finding that 74% of the audience were directly involved in addressing crypto crime, just 41% were familiar with address poisoning.
Andrew compared address poisoning to business email compromise scams, where spoofed addresses deceive victims. Attackers exploit wallet auto-fill and user habits via smart contracts, creating fake transactions with similar addresses, for instance, by subtly altering receiving addresses—such as changing “doe” to “d0e.”
These poisoned transactions initially appear in history, tricking users, especially during test transfers. The attacks, automated at scale, involve valueless tokens and complex infrastructure enabling thousands of simultaneous attempts.
Address poisoning case studies
Andrew detailed two major address poisoning cases:
• May 2023: The Drug Enforcement Agency (DEA) lost $55,000 in seized funds to an unknown hacker, demonstrating how even experts can be fooled.
• May 2024: $68 to $70 million was stolen after a 0.05 ETH test on May 3, 9:14 UTC. A fake ERC-20 token, “ETH,” mimicked the real Ethereum, and similar-looking addresses misled the victim.
The attacker’s smart contracts faked transfers, marking the most significant poisoning attack by initial value.
Address poisoning techniques and prevention
Andrew outlined three key components of address poisoning infrastructure:
• Smart contracts create fake “backwards transactions,” mimicking victim activity without stealing tokens.
• ERC-20 contracts impersonate real assets using identical symbols, are deployed briefly and rotated to evade detection.
• The attack scale is vast—Andrew found a single transaction with sixteen simultaneous poisonings, targeting varied token amounts and cryptocurrencies.
Examining one smart contract revealed 306 total transactions, but each could contain 16 to over 250 individual poisonings. Those 306 blockchain transfers could represent tens or hundreds of thousands of actual poisoning attempts—all executed within minutes of detecting suitable targets.
Address poisoning demands intensive computing power to monitor blockchains, identify targets, and brute-force matching addresses within seconds. The Secret Service’s wallet was poisoned amid 1,000 automated attempts, showing large-scale bot operations. Millions of attacks occur daily, costing approximately $4 per Ethereum attack but yielding huge profits. Cheaper blockchains lower costs further. Smart contracts reveal investigative clues, and the “fake USDT” confusion highlights the widespread and misunderstood nature of the attack.
Nick added that Crystal’s training students repeatedly ask about “fake USDT” in transaction histories, illuminating how common yet misunderstood this phenomenon remains.
Address poisoning recovery efforts
The panel discussed victim protection and recovery. Jonelle urged caution with all transactions, recommended exchanges that filter address poisoning, and questioned recovery rates—citing a $70M case where the victim recovered 90% of the stolen funds.
Andrew described fund returns as “not never, but somewhat infrequent,” noting nation-state actors seldom return assets since they’re “better set up to just take the money and run” due to their advanced technical infrastructure.
Address poisoning operates like a lottery, occasionally netting $20–70M. Andrew described a theft when the attacker wasn’t ready for such a windfall. Without a laundering infrastructure in place, the sudden gain became problematic. The victim’s message to the hackers—“We both know $7 million will definitely make your life better, but $70 million won’t let you sleep well”—combined implicit threat with realism about the difficulty of laundering.
The on-chain negotiation was remarkable. After a 10% bounty offer and a 24-hour ultimatum—”we haven’t posted anything on Twitter yet”—the victim spammed identical appeals to multiple addresses. One replied, resulting in restitution within a day, with a net loss of approximately $7M.
Adam from Inca Digital noted their civil litigation team rapidly pursues recovery, securing asset freezes within a week. Address poisoning cases surged from May to October 2025. Notably, victims now include government clients moving seized assets, demonstrating that even sophisticated role-players with blockchain experience remain vulnerable.
Introduction to risk washing
Jonelle introduced “risk washing,” explaining that investigators would be familiar with it in practice, although it’s not yet an industry-wide term in use. The discussion examined on-chain monitoring, basic typologies, and compliance challenges, explaining why illicit flows often evade detection by major platforms.
Understanding risk proximity and categories
Jonelle explained that Know Your Transaction (KYT) tools support exchanges in assessing the risks associated with deposits and withdrawals. Tools identify risks based on several factors, generating alerts that compliance teams investigate and escalate when necessary.
Risk proximity matters—some tools assess transaction hops, others exposure percentages. Categories include scams, fraud, blacklists, terrorism, sanctions, and Child Sexual Abuse Material (CSAM) for granular analysis.
Deposit analysis tracks the percentage of funds’ risk sources, central to risk washing by tracing customer deposits back to known threats.
Rescreening transactions and address cycling
Advanced exchanges use re-screening to catch post-deposit risks. Periodic lookbacks expose newly sanctioned addresses, countering tactics like Garantex’s address cycling.
When high-risk funds tied to terrorism, CSAM, or sanctions arise, compliance teams escalate, report, and isolate them. Quarantining the funds in separate wallets prevents co-mingling and supports potential asset freezes or seizures.
Jonelle stressed that risk engines differ substantially in capabilities, offering various rule and logic combinations.
Direct and indirect risk interactions in transaction monitoring
A crucial distinction exists between direct and indirect risk interactions:
- Direct risk interactions: Transactions directly from illicit actors (one hop), representing the highest-risk, immediate links to crime.
- Indirect risk interactions: Everything beyond direct; thresholds vary—some flag two or three hops, others track 100+ hops from the source.
Some tools use percentage exposure, not hops. For example, “5% of deposited funds trace back to the sanctioned entity, Garantex”, triggering alerts per exchange-set thresholds.
Threshold-based systems invite exploitation. From August to September 2024, Garantex tested exchanges by varying the number of hops and amounts to evade alerts, freezes, and due diligence triggers.
Risk washing techniques and examples
Jonelle used the example of a hop-agnostic tool needing $500 and 30% exposure; $400 at 25% bypasses alerts entirely. Criminals like Garantex exploit this loophole; Jonelle noted similar risk washing trends reported about Nobitex.
The example shows Garantex (100% risky) transferring to an intermediary rated 41% risky. Mixing deposits from regulated, unlicensed, and sanctioned sources dilutes exposure, sharply reducing the overall risk rating. However, this intermediary, labeled “non-custodial unknown address” in Crystal’s tool, may cluster with over-the-counter (OTC) desks elsewhere. If exchanges suppress alerts for centralized entities, significant Garantex exposure can go undetected.
Funds end at an address with 15% risk, often bypassing alerts or being dismissed as false positives. They then move freely into exchanges for withdrawal, fiat conversion, or further transfers.
Challenges in transaction monitoring
Jonelle noted that licensed exchanges aren’t complicit, but they face competing demands—managing alerts, false positives, and rule tuning—that require risk-based threshold settings across different exposure categories. Lowering thresholds to 5% or zero floods systems with false positives, strains resources, and freezes legitimate accounts, making balanced risk management essential.
Additionally, Garantex designations can be ex post facto. Even exchanges with very low risk thresholds wouldn’t necessarily catch activity initially if the addresses weren’t yet sanctioned. However, through re-screening processes—lookback procedures that reputable exchanges perform as a matter of course- these deposits would eventually be identified.
Nick noted that investigators often ask why exchanges accept deposits linked to Garantex or scams. He emphasized understanding the operational constraints, trade-offs, and complexities of exchanges rather than assuming negligence or complicity.
Andrew added a law enforcement perspective, describing a large-scale investigation where he traced Tornado Cash funds to a VASP. The ETH was swapped via DeFi to BSC before being deposited, creating an intermediary. Consequently, 100% exposure appeared from the swap service, masking the sanctioned origin.
Poll 3 asked the audience what VASPs can and should do to counter criminal attacks:
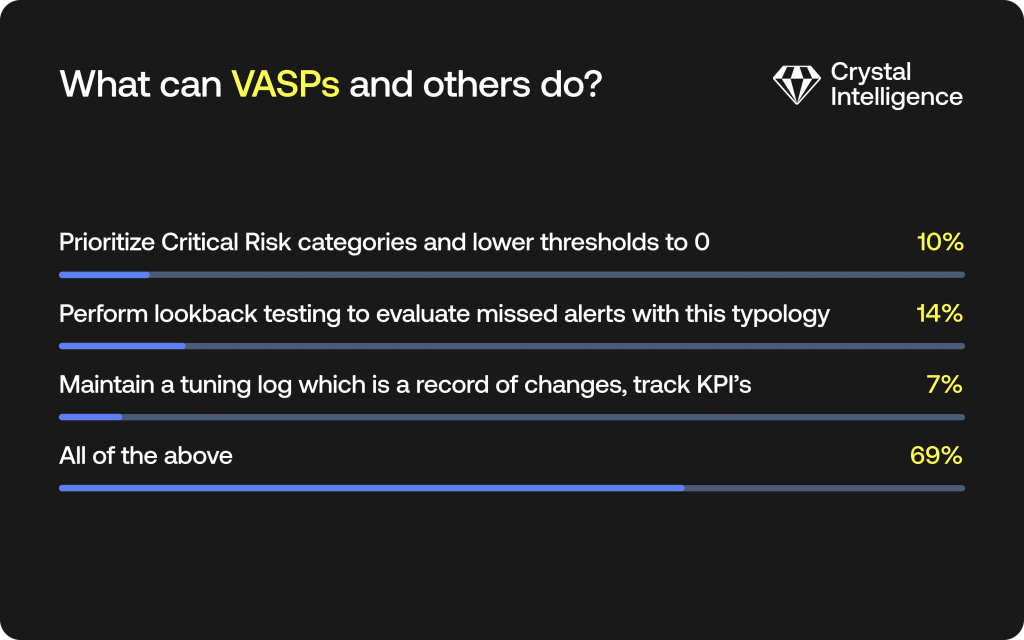
Overwhelmingly (69%), the audience felt that VASPs should employ a range of measures to combat crypto crime. Nick echoed this theme on the subject when he said, “One is none, two is one.”
Nick shared two key insights from Crystal:
• Use multiple tools—attribution varies, and single-source reliance causes blind spots.
• Grasp the context—risk scores alone aren’t enough; analyze fund origins and multi-hop exposures and understand the complete transaction flows.
Jonelle urged zero thresholds for terrorism, sanctions, and CSAM—any exposure should trigger alerts as industry best practice.
Bitcoin ATM vulnerabilities and banking exposure
Adam from Inca Digital discussed scam industry structures, noting the renewed relevance of Bitcoin ATM laundering as banks enter the crypto space under the GENIUS Act, emphasizing on-chain intelligence and closing illicit finance gaps. He said that Bitcoin ATM operators rely on banks for fiat rails, and Inca had found many smaller banks unknowingly service ATM networks, exposing risks through nested or correspondent banking structures.
Bankline and MSB Banking, for instance, link Bitcoin ATM operators to banks and cash handlers like Brinks, Garda, and Loomis, creating hidden exposure as community banks unknowingly bypass KYC on retail users.
While FinCEN urges vigilance for Bitcoin ATM activity, banks often lack insight into end-users, unknowingly servicing ATM networks through intermediaries.
The scale and criminal exploitation of Bitcoin ATMs
Adam from Inca cited significant compliance gaps and high fees, estimating that hundreds of millions of dollars were lost. Meanwhile, around 30 to 40,000 U.S. Bitcoin ATMs operate, with more being installed daily.
Adam highlighted the September 2025 the District of Columbia (DC) Attorney General’s lawsuit filed against Athena Bitcoin, where over 90% of deposits were tied to scams—mainly pig butchering schemes deceiving elderly victims into funding organized crime via Bitcoin ATM deposits.
Poll 4 asked the audience about victim age groups in Bitcoin ATM scams:
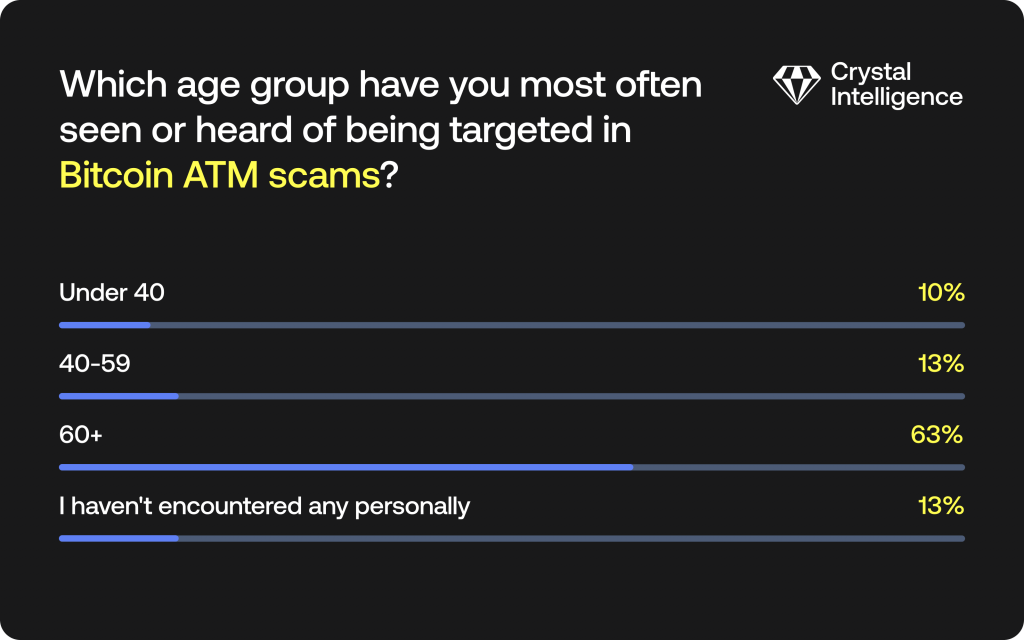
The law enforcement officer-heavy respondents found that 63% of the victims they had encountered were over 60 years old. Corroborating this, Adam added that in the Athena case in DC, the median age of victims was 71.
Using Inca and Crystal data, Adam’s team uncovered links between Bitcoin ATMs, mixers, Chinese OTC desks, and flagged addresses. These ATM funds merge into laundering networks supporting drugs, terrorism, and sanctions evasion.
Adam presented two transaction traces illustrating the scope of the problem:
- One showed ATM-linked inputs flowed into aggregator wallets, then to Paxful, Luno, and Boha—an unregistered Nigerian exchange often used in scam clusters.
- In another, two U.S. ATM transactions directly funded sanctioned wallets tied to Chinese laundering networks and synthetic opioid trafficking.
Poll 5- the final one- asked the audience how long they thought it took for Bitcoin ATM scam victims to realize they had been conned:
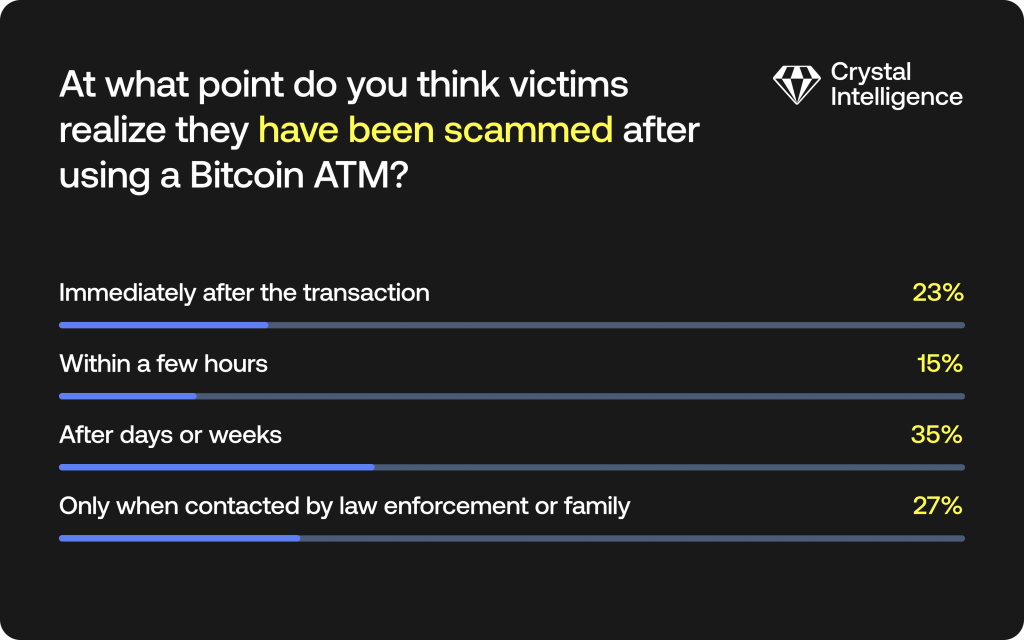
Sadly, 62% of respondents found that victims only learnt of their losses days or weeks later or when informed. Only 23% reported that victims realized straight away.
Geographical patterns of Bitcoin ATM scams & law enforcement responses
Nick stressed that, despite a growing focus on OTC desks, ATMs remain a vital cog in the crypto crime machine. Crystal’s data showed few OTC desks but many ATMs in North America, serving similar roles in scams and serious economic crimes.
Andrew called Bitcoin ATMs the “big bad wolf” of crypto crime, mostly illicit. Yet, their compliance teams are functional, and their Suspicious Activity Reports (SARs) provide investigators with valuable data.
Andrew also shared an innovative prevention approach, which involved posting scam-warning flyers on San Francisco Bitcoin ATMs regarding tax, kidnapping, and romance fraud. The low-cost campaign proved effective, and he encouraged local law enforcement agencies nationwide to adopt similar prevention efforts.
Jonelle added that the debate over categorizing Bitcoin ATMs is problematic. Each program requires merchant reviews and risk-based due diligence, taking into account compliance and reputation. Rather than imposing blanket bans, she urged enhanced monitoring, stricter reporting, and stronger oversight as banks expand into the crypto sector.
Conclusion and final thoughts on US crypto crime trends
The webinar provided tactical investigative guidance on three interconnected cryptocurrency crime typologies and offered strategic compliance perspectives on exchanges navigating competing pressures. It also highlighted systemic vulnerabilities that require urgent attention as traditional finance and cryptocurrency converge.
Nick concluded by thanking the panel for delivering comprehensive guidance for effectively identifying, investigating, and preventing financial crime across an increasingly complex digital asset ecosystem.
Watch the complete webinar discussion here:



