On February 21, 2025 at around 1420 UTC Bybit, a large international cryptocurrency exchange, suffered a security incident that resulted in the theft of over 400 000 ETH, worth around $1.4BN
The attack is notable not just in its size, but also in its sophistication.
Thieves were able to manipulate Bybit into approving a transaction that granted them control over their assets held in ‘cold storage.’ In effect, the attackers were able to replace Bybit’s vault keys with their own, giving them free access to whatever was held there. Once underway, Bybit was powerless to prevent funds from being siphoned away into the attacker’s control.
These forms of attack have become increasingly notable in recent times; WazirX and Phemex both reported similar methods used against them.
It began on a Friday, late in the day
The attack clearly targeted Bybit during a time when many services, including investigators, would have reduced staff able to respond to the incident. It began on a Friday, late in the day for many, including Bybit’s HQ in Dubai. Perhaps most significantly, it was our VP of Intelligence’s birthday weekend.
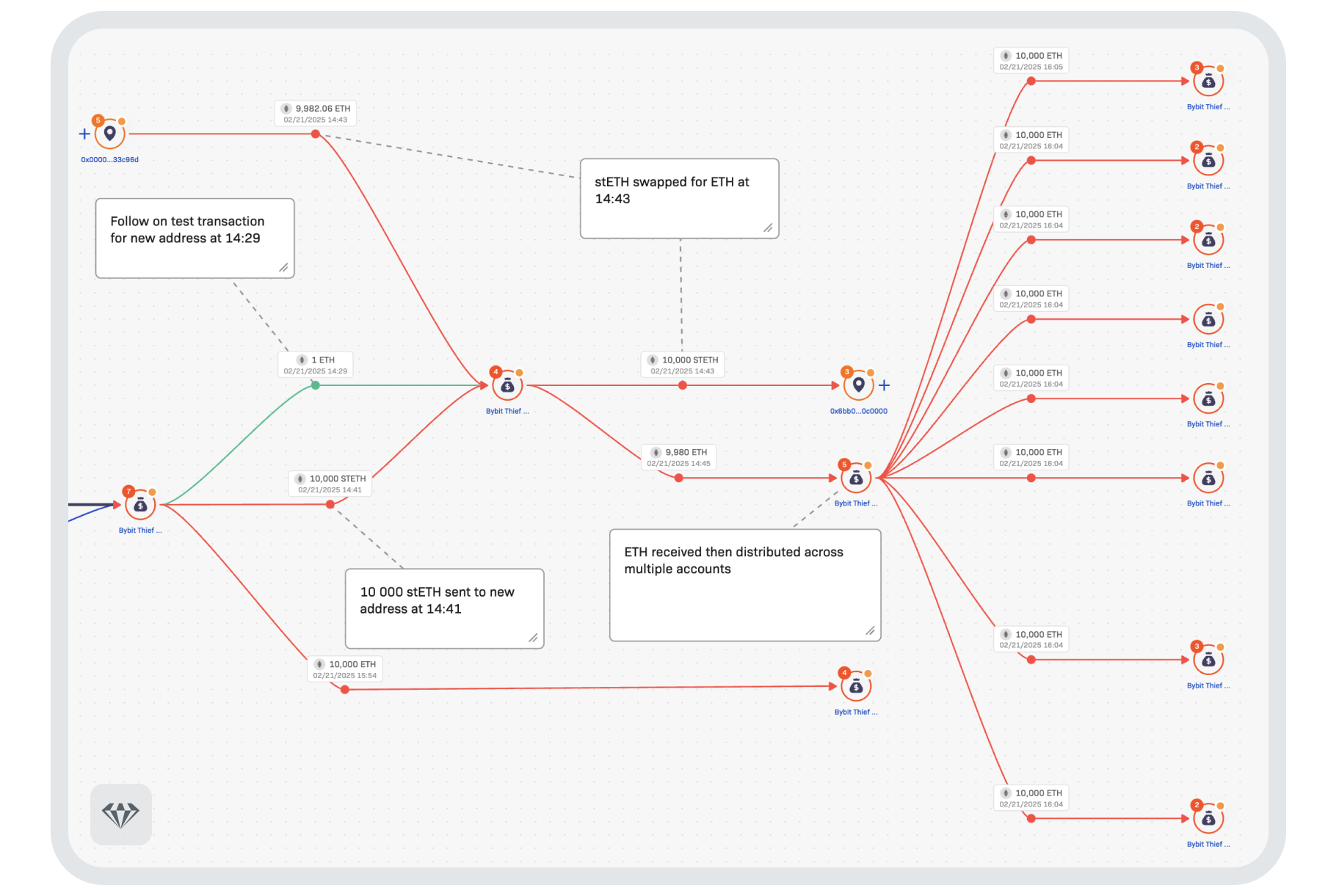
The attack started at 14:15 UTC with a mere 90 USDT transaction from Bybit to the thief – most likely a test to ensure that they had successfully compromised the system. One minute later, the floodgates opened with a withdrawal of 401,347 ETH, 90,375 stETH, 15,000 cmETH and 8,000mETH.

At 14:29, beginning with a test transaction of 1 ETH to a new address, and just 14 minutes after the attack had been executed, tokens (stETH, cmETH and mETH) were exchanged rapidly using decentralized finance services for Ethereum in batches of around 10 000. These tokens were then redistributed across multiple accounts. This took place in parallel across multiple addresses, suggesting a high level of organization and even automation of the process.
Initial reports of the incident began to surface almost an hour later; with confirmation from Bybit posted to the company’s X account at 15:51.
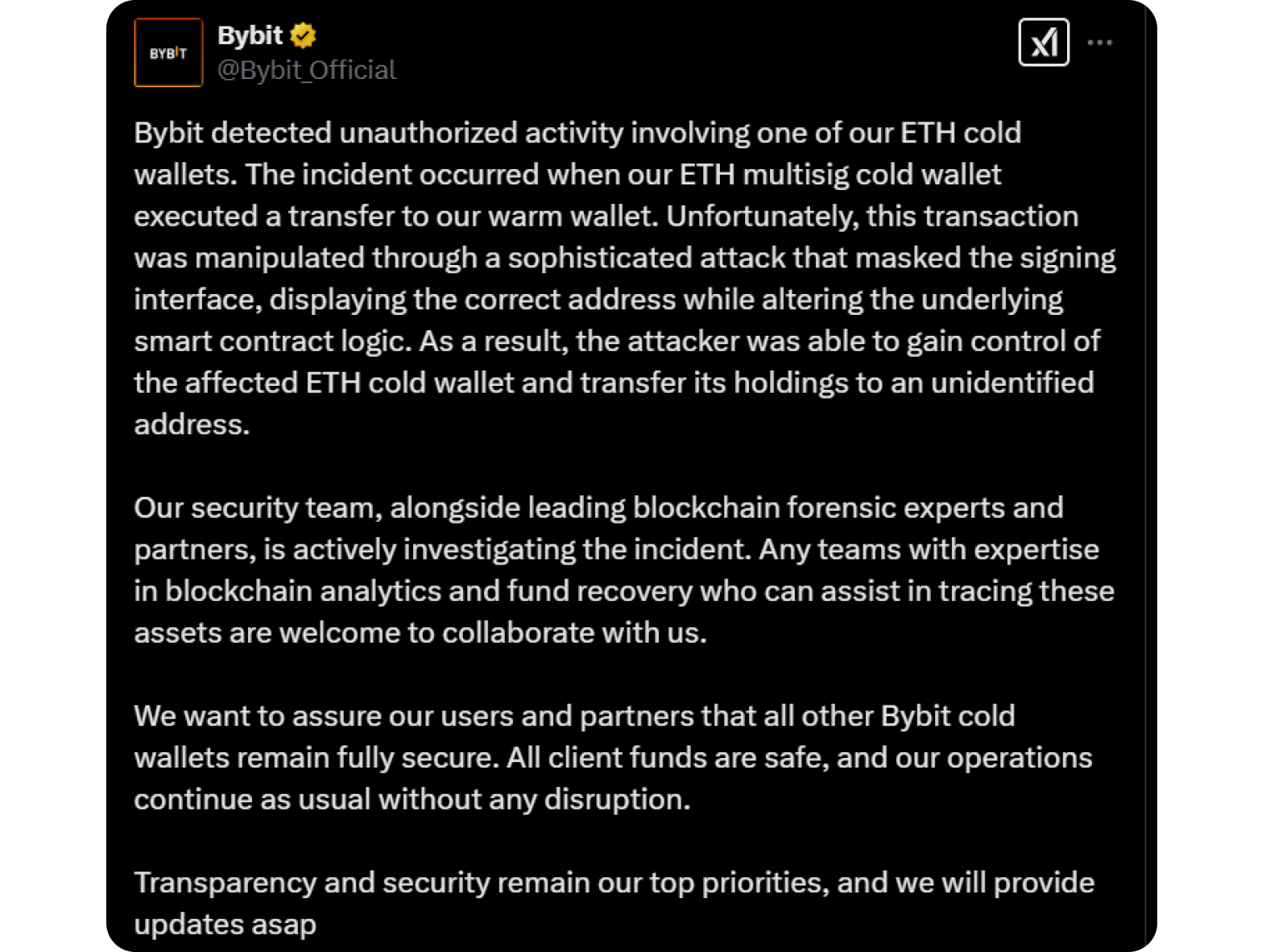
For many, the attack came as a complete surprise. It is not uncommon for exchanges to cycle funds from cold wallets when managing liquidity. Bybit raised the alarm early too, acknowledging the attack and calling across the industry for support in the recovery efforts.
The chase had begun. A race between investigators and thieves, that will continue for perhaps years to come.
Moving the money: help would be essential
Much of the funds remain in the initial wallets, untouched. Stealing such a vast sum of money comes with an equally large problem: converting it into another form without getting caught. Equally, such enormous amounts require a counterparty capable of handling it, as well as caution not to shift the entire cryptocurrency market.
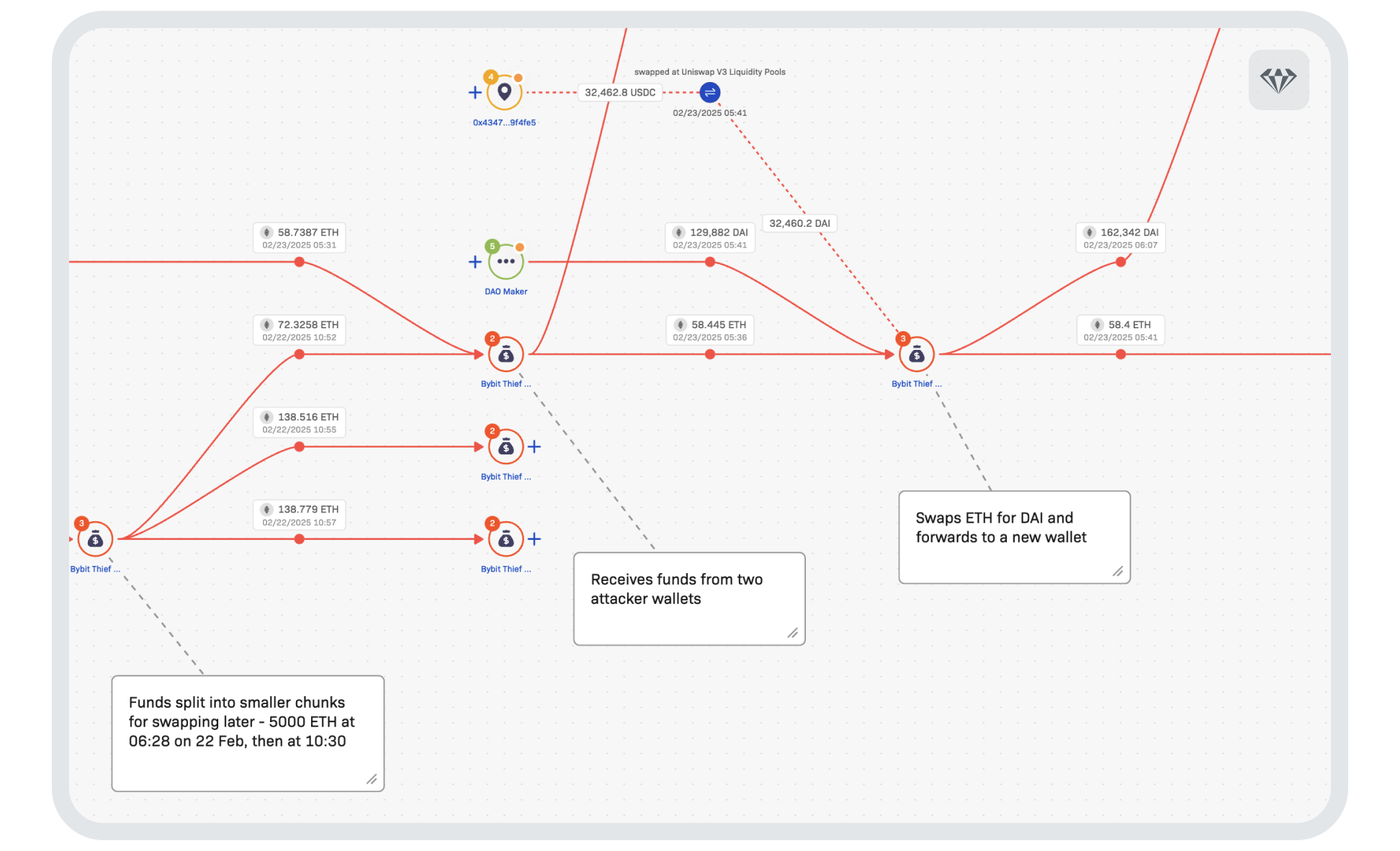
Therefore, breaking down the amount into smaller, more manageable chunks was the most sensible approach. This tactic also has the added bonus of overwhelming many of those trying to keep track. The thieves began siphoning the funds in batches into smaller and smaller amounts before swapping them in a variety of services, including Decentralised Finance platforms. In a tour of all blockchains, cross-chain bridges, tokens and services, they were swapping between all types in a flurry of activity.
As an example of this case’s complexity, the graphic below shows one of the preliminary stages the attacker conducts before moving the funds to a new blockchain. In it, funds are split into smaller amounts and swapped for DAI, a censorship-resistant stablecoin:
The DAI is then exchanged again for ETH, which is forwarded to new addresses as shown below.
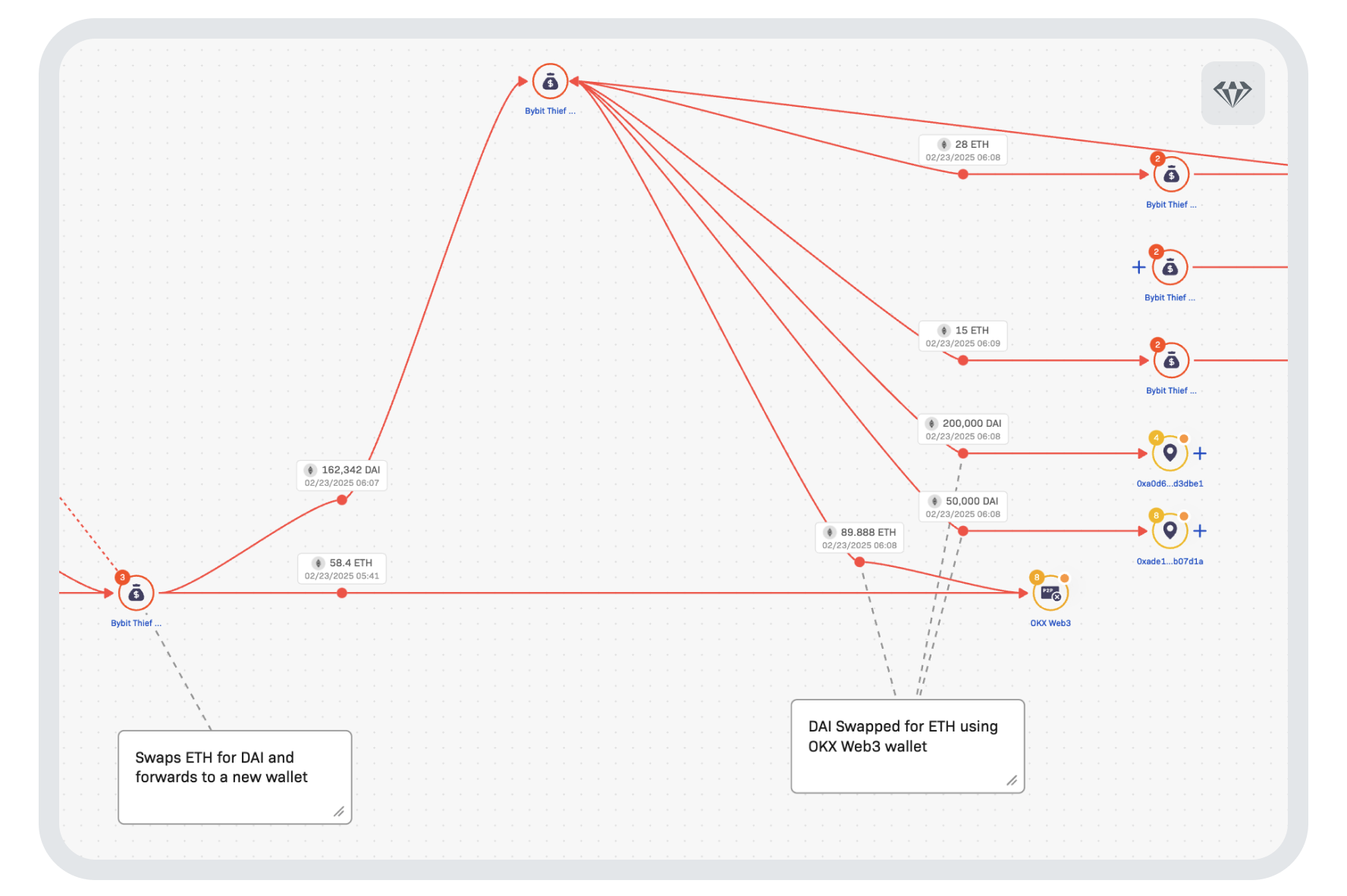
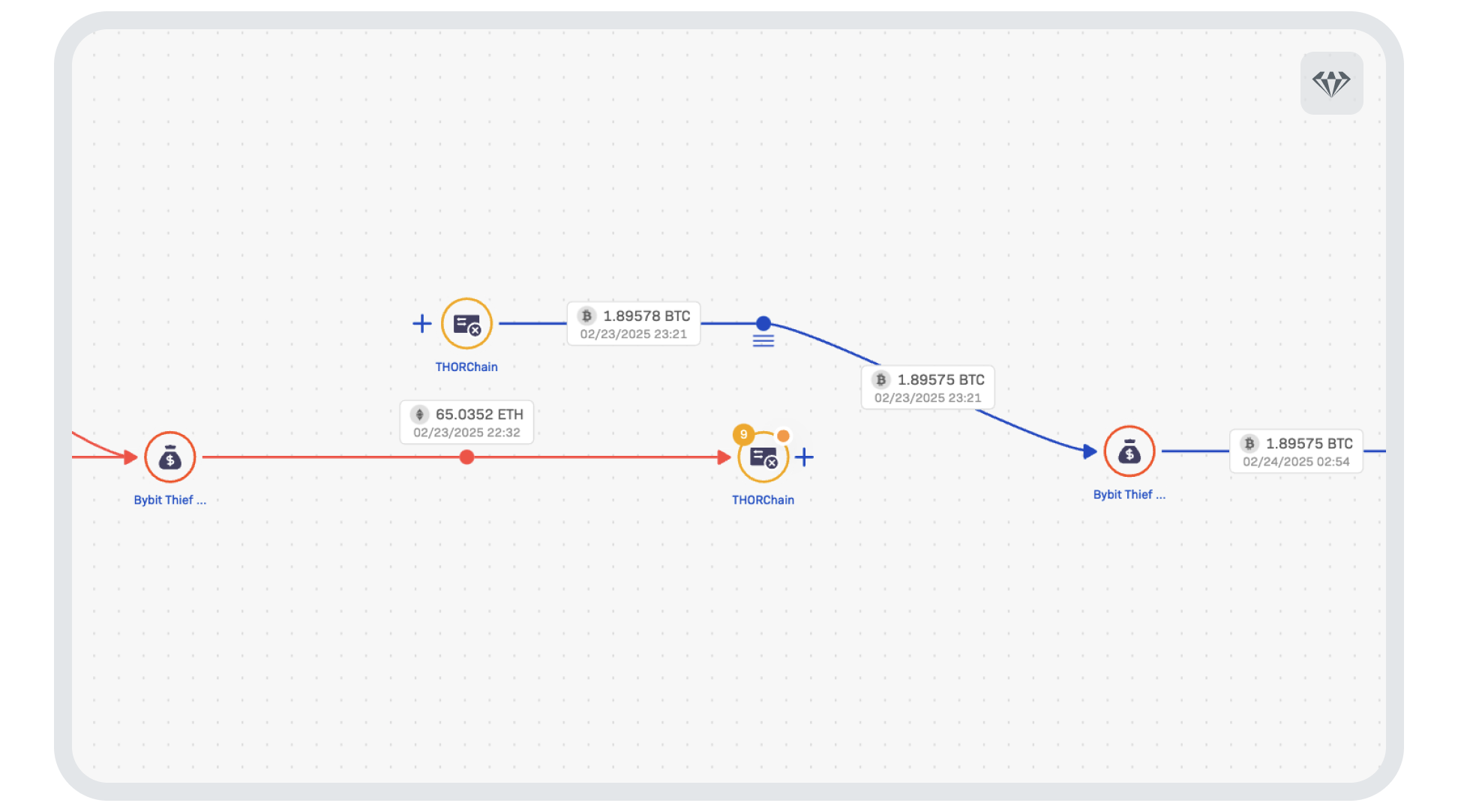
This is occurring in parallel with other swaps in other addresses. Not content with remaining with ETH, the attackers moved funds to the Bitcoin blockchain using popular cross–chain service THORchain shown below.
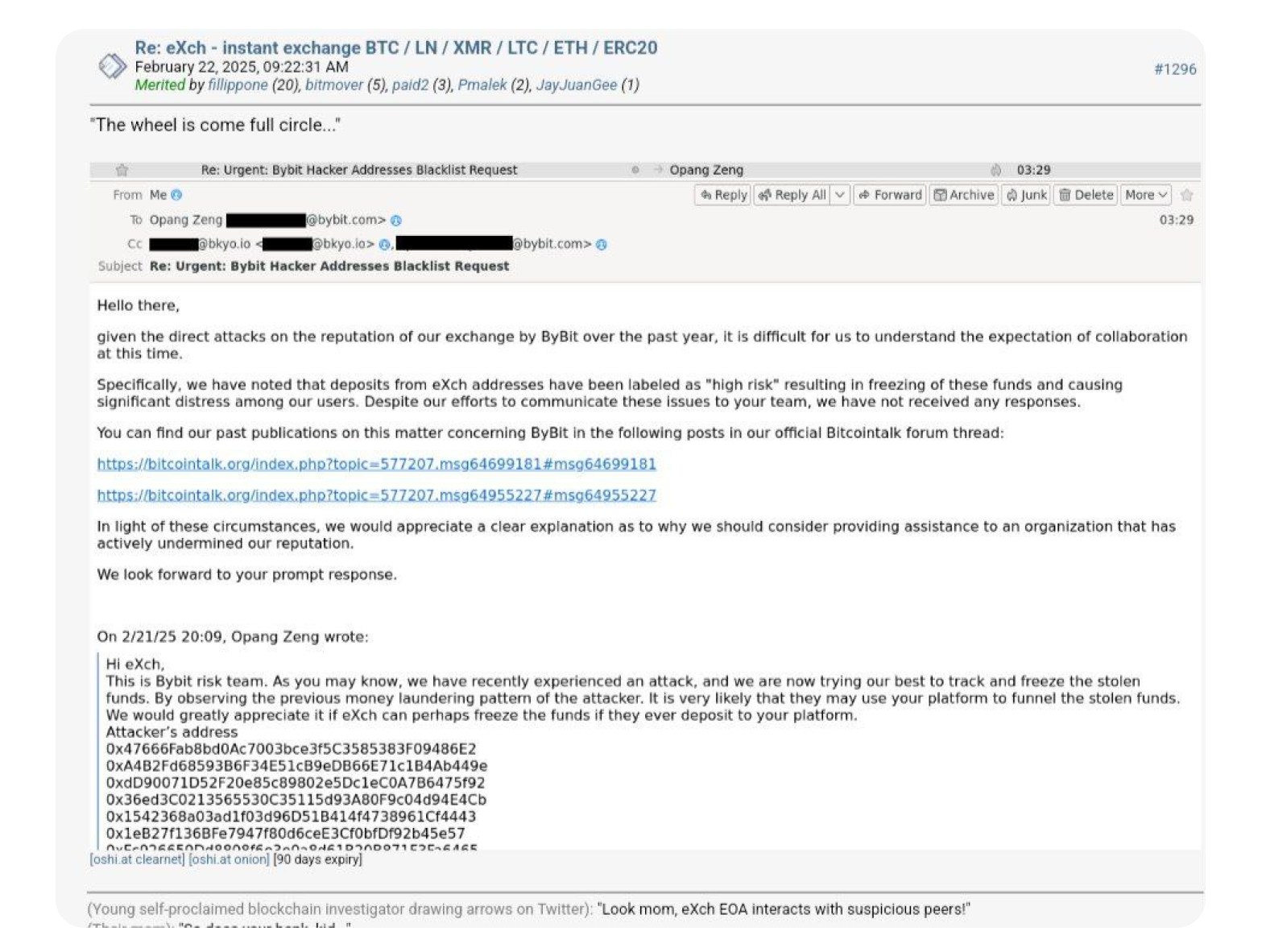
Another frequent source and destination of funds used by the attackers, though not generally attributable from a deposit transaction on-chain due to the nature of centralized services, is a proudly non-compliant service eXch. Crystal, along with many of our peer organizations, have noted considerable belligerence from this platform in previous cases much before this one.
Bybit’s choice to stop user withdrawals to eXch led to anger on the BitcoinTalk forum. eXch has also refused to support Bybit because it labeled the service as high-risk. The level of collusion between eXch and the thieves is not known, but this public statement is unlikely to convince many that eXch are not involved in some capacity.
Generally, funds are being split into amounts of less than $100,000 worth of the target currency, with test transactions as low as $10 being sent to Exchanges, most likely using fake or compromised accounts. If we assume that will be the case, then there are at least 14,000 transactions to monitor and intercept.
Crystal responded to this unique event by standing up a crisis response team, which is working tirelessly around the clock to track developments and fund movements. So far, our expert team has labeled over 1,000 addresses involved in the case, a number that is growing with additional data sources provided by our industry partners and Bybit themselves.




