On July 18, 2024, a significant security breach occurred at WazirX, a leading cryptocurrency exchange based in India.
WazirX, India’s largest domestic cryptocurrency exchange, had approximately 50% of its assets, amounting to over $230 million, stolen from one of its main trading wallets by criminals despite having robust security measures in place to prevent such an occurrence.
The breach resulted in a loss of over INR 1900 crores (approximately $230 million). This incident is of great importance in the cryptocurrency industry, particularly within India.
In this blog, we examine the breach in more detail. We provide a detailed analysis of the breach, evaluate the existing security protocols, and assess the broader impact on the cryptocurrency landscape.
Who is WazirX?
WazirX was founded in 2018 by Nischal Shetty, Siddharth Menon, and Sameer Mhatre to cater to the growing Indian cryptocurrency market. The company has gained a positive reputation for its pro-compliance and pro-regulatory stance. Additionally, it regularly publishes transparency reports on its AML efforts, regulatory compliance, and technological advancements, contributing to a favorable impression among Indian users.
When did the WazirX hack occur?
On July 18, 2024, at 06:19 AM, Universal Coordinated Time (UTC), a WazirX Ethereum Hot Wallet was drained of all its tokens.
The affected Ethereum Wallet Address is: 0x27fD43BABfbe83a81d14665b1a6fB8030A60C9b4
If you are a Crystal client, you can view the address here.
What occurred during the breach?
The breach occurred as a result of a sophisticated attack that involved modifying the required signatures to authorize transactions from the hot wallet to one controlled by the attacker. This was achieved by the hacker persuading multiple current signatories to alter a smart contract that would have otherwise prevented this unauthorized activity.
Crystal responded to this event at 06:48 AM UTC blocklisting the destination address used by the thief. Immediately understanding the scale of the attack, our proactive investigations team began monitoring the event and commenced support.
What was the WazirX response?
In response to the cyberattack, WazirX opted to freeze all trading and withdrawals on the platform while it worked to resolve the issue – this freeze is still ongoing.
How did the WazirXbreach happen?
At this stage, there is no conclusive proof of how the attack was carried out.
However, we do know the sequence of events that allowed the attack to occur on-chain. It is also evident that the attacker had the necessary skill to bypass the rigorous security controls in place.
According to WazirX’s public statements, the hot wallet was managed using Liminal’s digital asset custody and wallet infrastructure and was secured with multiple signatures. This means that a specified number and type of users were needed to approve a transaction for it to take place.
A simple way to visualize this is like a door with multiple locks. To open it, you need to have a minimum number of keys.

Above: Figure illustrating multi-sig wallets
In the case of WazirX, four out of six signatures were required—three from WazirX and one from its custodian, Liminal. As an extra layer of security, WazirX’s keys are held on hardware devices that are not connected to the internet and cannot be easily compromised, even if the device itself is stolen.
Knowing that any transaction would need four of six signatures, the attackers deceived WazirX and Liminal into approving a smart contract that would transfer control to them.
Where did the stolen WazirX crypto funds go?
Using Crystal’s blockchain analytics and monitoring solution, our investigators were able to determine how the hacker dispersed the funds and have demonstrated the flow using our visualization tool.

After taking control of the WazirX wallet, the attacker systematically drained it. However, we were able to show that the thief was preparing his moves before the attack. On July 10th, 2024, eight days before the attack the WazirX thief was funded via Tornado Cash.

At the time of the attack on July 18th, the hacker drained the compromised WazirX wallet of $230m.

After the attack, the hacker distributed the funds via a couple of wallets and started swapping tokens for ETH.

The hacker also sent funds to ChangeNOW which blocked the transaction, and BInance, where funds were also most likely blocked.
Who was behind the attack?
There is no hard evidence as to who is behind the attack.Some experts speculate that North Korean hackers, specifically APT-28, a well-known criminal group known as Lazarus, are behind the hack. The Lazarus group has historically executed complicated heists and stolen millions of dollars.
What could WazirX have done to prevent this?
Given we don’t know what really led to the attack’s success or how the attackers managed to get past the four signatories, technical recommendations are speculative. However, WazirX released a statement on August 19, 2024, regarding the findings of a forensic analysis conducted by cybersecurity firm Mandiant.The analysis aimed to determine whether any of the three laptops used by WazirX team members for transactions had been compromised.
Mandiant concluded their investigation by stating, “We did not find evidence of compromise on the three laptops used for signing transactions.”
While this may be the case, the fact remains that of the four signatures required, three were WazirX signatures, so the question still remains as to how the attacker managed to successfully get past these.
Insights from Nemean
Karl Mackenzie from London-based digital assets security firm Nemean explains how multi-sig wallets work, what went wrong for WazirX and what other factors can contribute to a security breach
What is a multi-sig wallet and why does it matter?
Multi-signature wallets have become popular among retail and institutional cryptocurrency investors because these wallets offer a high level of security and transaction functionality. However, they are not without risks.
The security of multi-signature wallets can be compromised if the private key data is distributed in an insufficient protocol or if the private keys are not stored and managed correctly. If malicious third parties gain access to one or more private keys—as in the case of WazirX—it can lead to loss of access or even complete loss of funds in wallets that use multi-signature technology.
How to ensure optimal security with a multi-sig wallet
To secure multi-signature wallets, the access to private keys is distributed among multiple distinct entities.
It is important to distribute private key data securely to trusted parties and store it safely. The threshold for transactions (Majority of Number) should remain high to ensure that the security of the wallet is not compromised if one or more private keys are lost.
Geographical or virtual separation of the private keys is also an effective way to prevent multiple keys from being accessed simultaneously.
A key aspect of ensuring the security of multi-signature wallets is the end-to-end encrypted sessions for wallet creation and private key distribution. Private key data should be distributed to multiple trusted parties, ideally a large number of individuals who store the data separately.
Storage solutions used by exchanges, institutions, or investors are also crucial in preventing hacks. Hot or warm storage on cloud-based applications increases the risk of data access online. On the other hand, air-gapped cold storage and encrypted hardware devices significantly reduce the risk of hackers accessing private key data.
Appointing trusted third parties for data storage or seeking security compliance expertise before creating the wallet and generating private keys can guarantee secure and correct data storage.
What went wrong for WazirX
Insecure distribution of private keys
It appears the hackers knew that keys were only distributed between two organizations and meticulously planned how to deceive both organizations to acquire the signatures. WazirX has subsequently reported that the three keys were distributed on Ledger Hardware Wallets.
It is possible by penetrating the multi-sig protocol, the hackers were able to access multiple private keys associated with different wallets through the compromise of ‘key generation sessions’ or ‘wallet creation sessions’.
If this were the case, it would have led to a systemic failure of their wallet infrastructure, potentially enabling a prolonged period of unauthorized access to client wallets by malicious parties. Hackers may have been able to intercept and retain copies of private keys from multiple sessions and, later, execute a coordinated attack to gain access to multiple wallets.
Threshold of required signatures was achieved
Multi-sig wallets, by name, require multiple signatures from different approved users to settle transactions. In multi-sig wallets, transaction thresholds should be greater than 1. That is, the greater the Majority of the Number (MofN), the more protected the wallet is.
In the case of WazirX and Liminal, four out of six signatures were needed for the transfer to be approved.
According to the WazirX statement:
“The wallet had six signatories—five from our WazirX team and one from Liminal, who were responsible for transaction verifications. A transaction typically requires approval from three of the WazirX signatories (all three of whom use Ledger Hardware Wallets for security), followed by the final approval from Liminal’s signatory. A policy to whitelist destination addresses was also in place to enhance security. These whitelisted addresses were earmarked and facilitated on the interface by Liminal; consequently, the WazirX team had the ability to initiate transactions to the said whitelisted addresses.
Unfortunately, the hackers successfully gained the required number of signatures by deceiving the private key holders. Armed with these signatures, the hackers were able to access the wallet and drain the funds. Once the data was stolen, both organizations were powerless to prevent the theft.
How will the stolen funds be used?
Finally, and most importantly, there is significant concern about the potential use of the stolen funds.
In many security breaches, stolen funds are often used to finance further criminal activities, such as ransomware attacks, the funding of illicit goods and services, or even state-sponsored cyber operations, as is often speculated in cases involving groups like the Lazarus Group.
Right now, we know the funds are being held in these wallets:
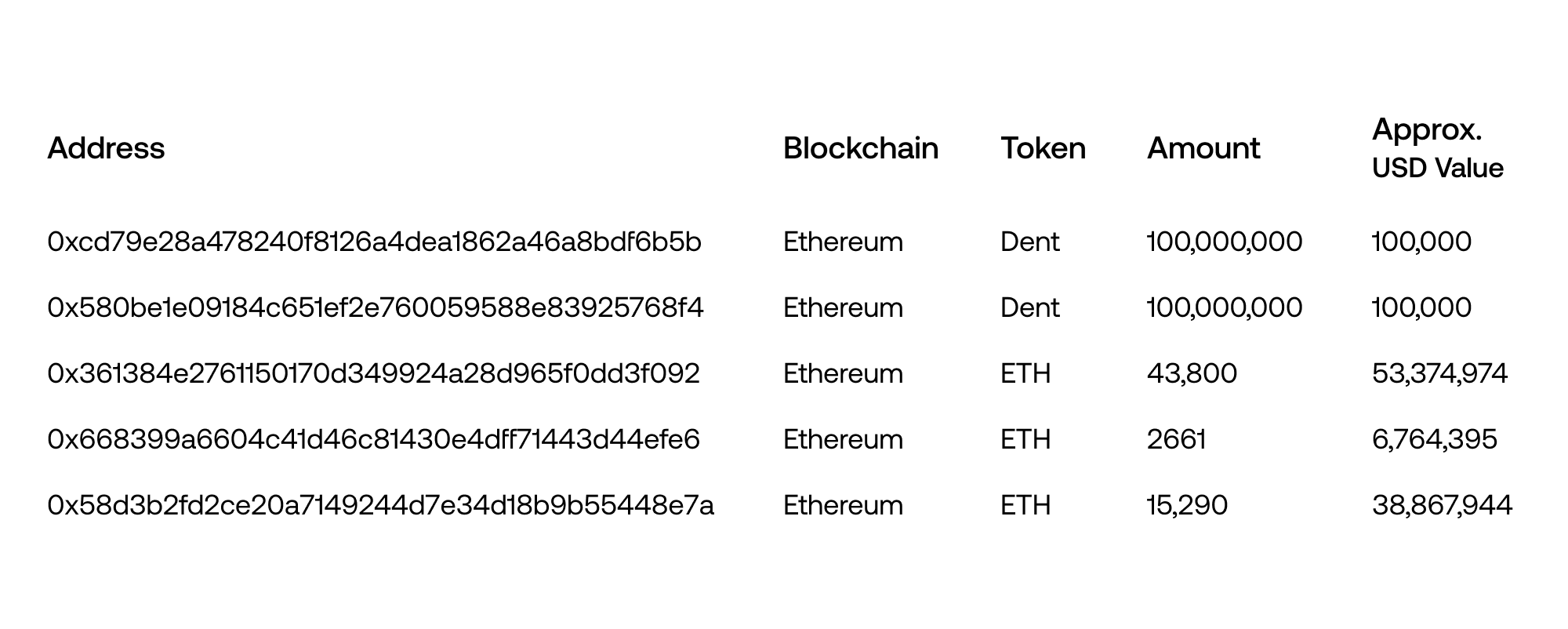
Latest updates
On Monday, September 2, 2024 at 15:08:47 UTC we were alerted that the WazirX hacker was moving funds to Tornado Cash.
This started with a test transaction of 0.1ETH.
Then 2600ETH – around $6,5m – was sent to the 100ETH deposit address on Tornado Cash.

Glossary
Air-gapped Cold Storage
A security measure where a device holding cryptocurrency private keys is kept offline and isolated from any network, preventing unauthorized access.
Blockchain
A decentralized digital ledger that records transactions across many computers in such a way that the registered transactions cannot be altered retroactively.
Cryptocurrency
Digital or virtual currencies that use cryptography for security and operate independently of a central bank. Examples include Bitcoin, Ethereum, and many others.
Custodian
An entity responsible for holding and safeguarding an institution’s or individual’s digital assets, such as cryptocurrency, on behalf of the owner.
Hot Wallet
A cryptocurrency wallet that is connected to the internet, allowing for quick and easy access to funds but making it more vulnerable to cyberattacks.
Key Generation Session
The process in which cryptographic keys (such as private keys for a multisig wallet) are generated, ideally in a secure, encrypted environment.
Lazarus Group (APT-28)
A North Korean cybercrime group known for its sophisticated cyberattacks, particularly on financial institutions, including cryptocurrency exchanges.
Multisig Wallet (Multi-signature Wallet)
A cryptocurrency wallet that requires multiple private keys to authorize a transaction, increasing security by distributing control among several entities.
Private Key
A secret alphanumeric password or code used in cryptography, granting its holder access to the funds in a cryptocurrency wallet.
Security Breach
An incident where unauthorized access to data, applications, services, networks, or devices occurs, leading to the possible theft or misuse of information.
Smart Contract
A self-executing contract with the terms of the agreement between buyer and seller directly written into lines of code, which automatically executes when predefined conditions are met.
Tornado Cash
A privacy tool that helps users in cryptocurrency transactions to obscure the origin and destination of their funds by pooling transactions together.
Wallet Draining
The act of emptying a cryptocurrency wallet by transferring its contents to another wallet, usually by an unauthorized party during a security breach.



