We previously wrote an in-depth analysis of the WazirX hack, detailing how the perpetrators began laundering the stolen funds. If you missed that discussion, you can read it here.
In this article, we’re delving further into the sophisticated techniques used by the cybercriminals behind this hack, focusing on how they hid their tracks and leveraged complex strategies to remove the connection between the stolen assets and the original breach. Their ultimate goal? To evade detection and cash out without raising standard AML/CFT red flags.
We’re going to analyze the laundering methods used, from privacy-focused tools and decentralized exchanges, to layering transactions through numerous wallets. We’ll also explore how they adapted their tactics to overcome the challenges posed by blockchain transparency, and the role regulatory gaps played in enabling their activities. Understanding these strategies is crucial for compliance professionals and investigators to help strengthen their defenses against similar threats in the future.
What Is Tornado Cash?
As we’ve seen before, the attackers took advantage of Tornardo Cash to launder their funds. This is a decentralized, non-custodial protocol that enables users to mix their cryptocurrency transactions, making it significantly harder to trace funds from the source to the destination. Built on Ethereum, Tornado Cash leverages zero-knowledge proofs to enhance privacy, allowing users to deposit and withdraw Ether (ETH) or ERC-20 tokens in a way that hides the connection between the sender and recipient.
Understanding “pools” in Tornado Cash
Tornado Cash offers a unique way to preserve privacy when moving funds on the blockchain. Since this was the token used in this criminal scheme, let’s analyse how Tornado Cash manages Ether (ETH).
One of the key features of the protocol is its use of fixed deposit pools for transactions. These pools, for ETH, are set at 0.1 ETH, 1 ETH, 10 ETH, and 100 ETH, and are essential to Tornado Cash’s functionality and its ability to provide privacy.
But why does Tornado Cash use these specific denominations, and how do they contribute to its anonymizing effect? Let’s break it down.

Visualization of Tornado Cash pools
The concept behind fixed pools
In traditional transactions, the amount of funds being sent can serve as a clue to traceable patterns. If someone deposits exactly 111.4 ETH into Tornado Cash and later withdraws exactly 111. 4 ETH, even with the privacy tools in place, it would be relatively easy to connect the dots between the deposit and withdrawal. To solve this, Tornado Cash introduces fixed denomination pools.
These fixed pools mean that users can only deposit and withdraw amounts in these specific sizes. By restricting the deposit and withdrawal amounts to these uniform values, Tornado Cash makes their transactions even more anonymous. For example:
- If you deposit 1 ETH, it goes into the 1 ETH pool along with all other users who deposited the same amount.
- If you deposit 10 ETH, it goes into the 10 ETH pool, and so on.
In the example above, a user wanting to mix 111.4 ETH, will make the following transactions to Tornado Cash:
- 1 transaction to the 100 ETH pool,
- 1 transaction to the 10 ETH pool,
- 1 transaction to the 1 ETH pool and
- 4 transactions to the 0.1 ETH pool.
The larger the number of people who deposit into the same pool, the more difficult it becomes for anyone (including investigators or blockchain analysts) to trace which deposit is linked to which withdrawal.
Mixing and anonymizing: Once the funds are deposited, they get mixed with all other deposits in the same pool. Because the amounts are uniform (e.g., every deposit in the 1 ETH pool is exactly 1 ETH), there’s no way to distinguish one deposit from another.
Withdrawal: When you want to withdraw your funds, you can do so at a later time to a completely different wallet, but only in the same predefined amounts, 0.1 ETH, 1 ETH, 10 ETH, or 100 ETH (minus fees). By making sure that the amounts are identical and predetermined, Tornado Cash makes it much harder to track funds as they leave the system.
However, the core element that enables Tornado Cash to provide privacy is the concept of anonymity sets. Simply put, the more users who are participating in the same denomination pool, the harder it becomes to trace any individual’s funds. On the flip side, when fewer people use a pool, the level of anonymity goes down, making it easier to correlate transactions and potentially deanonymize users.
But even a privacy solution can have its limits. When you attempt to launder a significant amount, such as $230 million USD, regardless of the liquidity and capacity of the mixing service, your activity will still stand outt. This was precisely the case with the WazirX exploit.
While the smaller ETH pools—such as the 0.1 ETH and 1 ETH pools—see substantial traffic, with hundreds of users making deposits and withdrawals daily, the 100 ETH pool tells a different story. Only a small percentage of users can afford to use this pool, given that 100 ETH (at the time of writing) is valued at approximately $265,000 USD. As a result, the attackers behind the WazirX exploit stood out by overwhelming Tornado Cash with massive amounts of illicit funds.
Based on our investigative findings, on September 10, 2024, a staggering 98% of all incoming funds to Tornado Cash were tied to the WazirX attackers. This sheer volume of transactions, especially in the 100 ETH bucket, drew significant attention, weakening their efforts to blend in.
Furthermore, the withdrawals from Tornado Cash linked to these criminals exhibited several distinct patterns, all laundering the approximately 99.5 ETH received from Tornado Cash. Let us look at some of them.
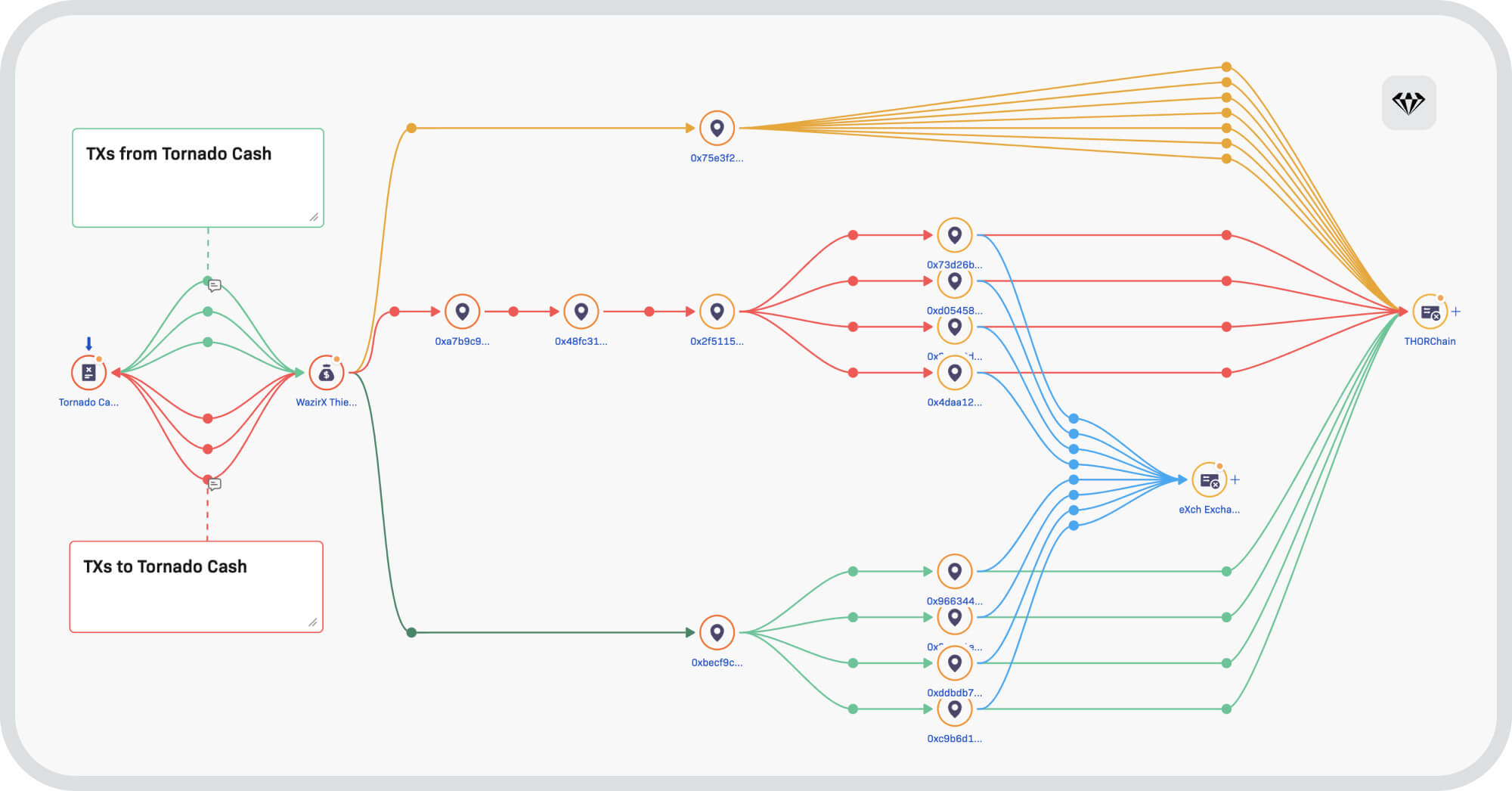
- The yellow pattern shows the sending of ±99.5 ETH to an intermediate address, which then makes 6-7 transactions to THORChain.
- The red pattern transfers ±99.5 ETH through 3 intermediate hops, before splitting the funds through 4 different addresses which then deposit to THORChain.
- The green pattern directly splits the ±99.5 ETH through 4 different addresses (without intermediate hops) which then deposit to THORChain.
- The red and green patterns also involve 4 deposits to a centralized unlicensed exchange (in light blue).
This illustrates another example of the pattern. Like the previous ones, it combines funds from several addresses and finally deposits to THORChain. These graphs don’t necessarily show all the inputs and outputs received, nor all the patterns used by the criminals, but give a good example of both.
As seen above, many of the patterns used by the criminals behind the hack involve the use of swaps through a service called THORChain. THORChain is a decentralized cross-chain liquidity protocol that allows users to swap native assets across different blockchains, all without needing wrapped assets or relying on centralized exchanges. It also lets users trade cryptocurrencies from different blockchains (such as Bitcoin, Ethereum, Binance Chain, etc.) directly and natively.
How Does THORChain Enable Cross-Chain Swaps?
THORChain uses a combination of its native token RUNE and a network of liquidity pools to facilitate these cross-chain swaps. Here’s a simplified breakdown of the process. Let’s imagine a user wanting to swap Bitcoin (BTC) for Ethereum (ETH). The user interacts with THORChain’s interface (or a supported front-end application) and selects the assets for the swap.
- Liquidity Pools: THORChain operates liquidity pools for various assets on different blockchains, with each pool containing the native asset (e.g., BTC) and THORChain’s native token, RUNE. The pools work by matching users who want to swap different assets.
- RUNE as the Settlement Asset: All swaps on THORChain are routed through RUNE. This means that when a user swaps BTC for ETH, the transaction involves two swaps behind the scenes:
- BTC is swapped for RUNE in the BTC-RUNE liquidity pool.
- RUNE is swapped for ETH in the RUNE-ETH liquidity pool.
Once both swaps are completed, the network sends the user the native ETH to their Ethereum wallet. At no point does the user need to deal with wrapped tokens or interact with an intermediary.
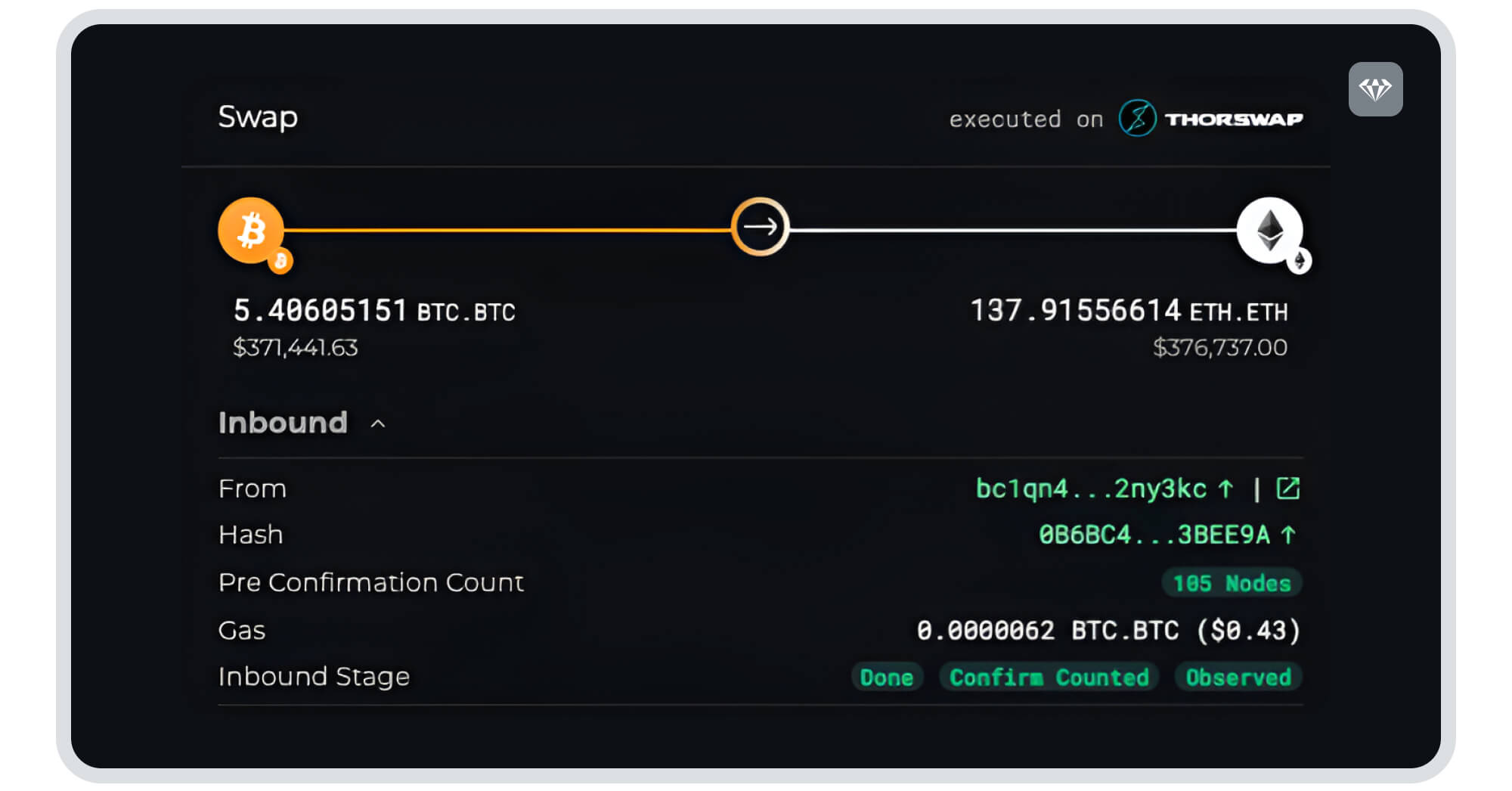
Crystal conducted an in-depth analysis of the transaction initiated by the attacker, which involved the movement of funds from Tornado Cash, through a series of intermediate addresses, ultimately reaching THORChain, with the platform’s explorer providing a robust tool for tracking these types of activities. Once the transaction hash is input, the explorer offers a comprehensive view of the executed swap, detailing the cryptocurrency acquired and the recipient’s address.
The image provided above is an example of such a transaction flow. It illustrates the Ethereum (ETH) sent into the swap and the corresponding Bitcoin (BTC) obtained post-swap. The explorer allows analysts to pinpoint both the exact assets involved in the exchange and the final destination of the funds. This functionality is crucial in tracing suspicious activities and mapping the transfer path, particularly when malicious actors attempt to obscure their tracks using multiple intermediaries or privacy-centric services.
Once the number of swaps is detected, analyzed and traced on a graph, a clear pattern emerges which is repeated over and over again.
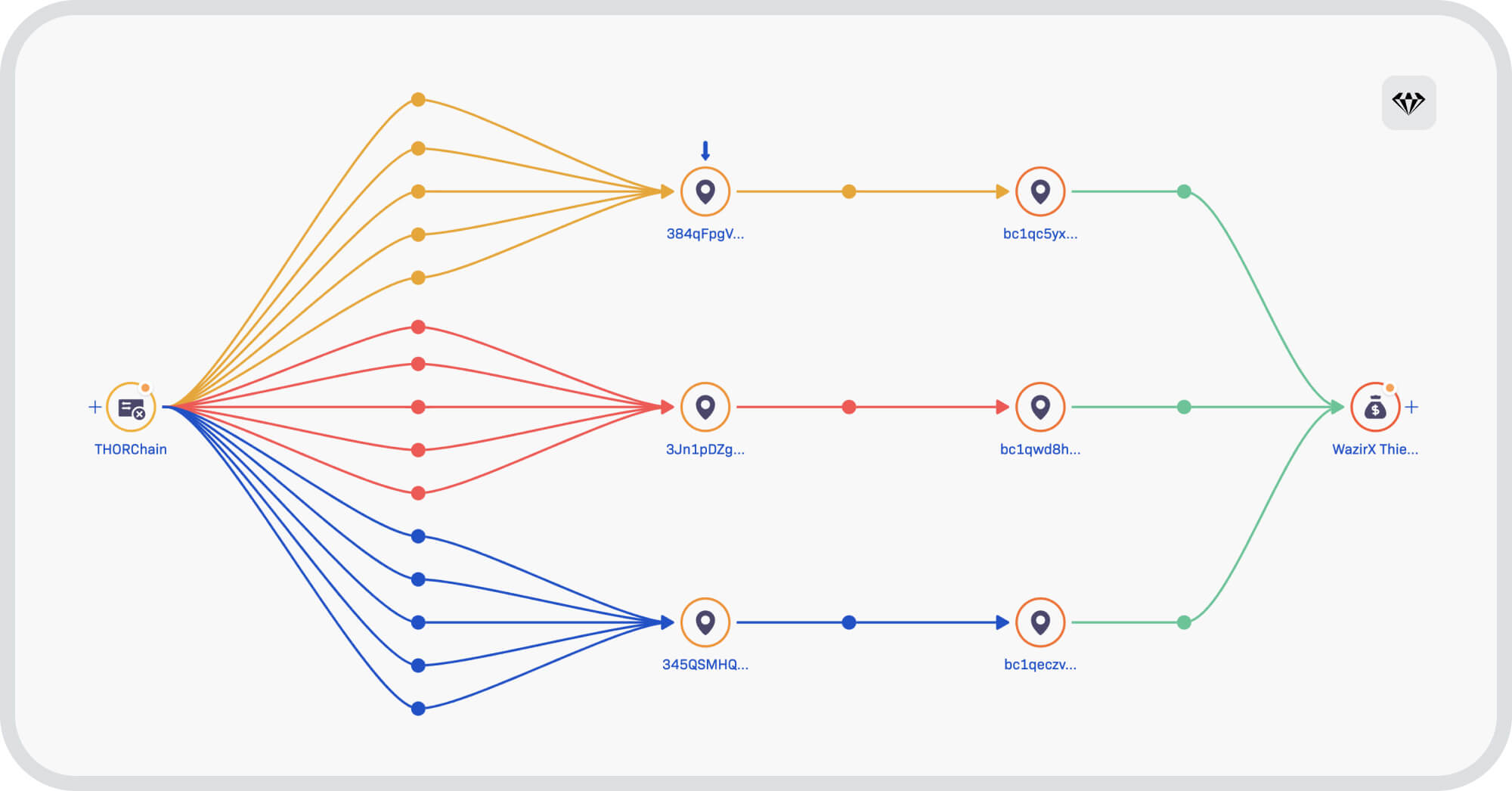
Example of pattern from THORChain where BTC go back to the attacker
While the analysis described has provided valuable insights into the attacker’s movement of funds through Tornado Cash and into THORChain, this is by no means the end of the investigation. We are now entering a new phase where the focus shifts towards tracking the flow of Bitcoin (BTC) obtained through these swaps.
A portion of the stolen funds—amounting to hundreds of Bitcoins— are now sitting unmoved in different bitcoin addresses, or ‘settled’, as we say, but a significant portion remains in motion, currently being laundered through privacy-enhancing services such as Wasabi Wallet.
At the same time, other portions of the funds have again passed through THORChain, this time being swapped back into Ethereum (ETH), further complicating the tracing process.
As we continue to track these activities, the investigation remains dynamic. Each phase of fund movement presents new challenges, requiring vigilance and the use of advanced tools to follow the increasingly complex web of transactions.
For LE the ultimate goal remains clear: to trace the stolen assets to their final destinations, identify the perpetrators, and uncover any potential connections to larger networks of illicit activity.
The investigation is far from over. It’s a fluid and evolving process that will need continued attention as the attacker attempts to obscure their tracks. Crystal remains vigilant for any new tactics that may be employed to further obfuscate the movement of stolen funds.



