Crystal Intelligence held this webinar to discuss the massive financial losses due to cybercrime, the relevance of cryptocurrency crime statistics, and ongoing fraud detection and prevention challenges. They tackled questions about regulatory efforts, law enforcement’s role, the measures exchanges must adopt to keep themselves safe, and how the industry can counter hacks and scams in the future.
The meeting was led by Crystal Chief of Intelligence, Nick Smart, who discussed the evolution of crypto hacks and scams with Andrii Sovershennyi, Lead Investigations Analyst at Crystal. The panelists also ran several polls to test the audience’s views on various crypto-related issues, with fascinating results!
Both experts urged exchanges, regulators, and compliance teams to embody the Scouts’ motto “Be prepared” by anticipating incidents, rehearsing responses, responding proportionately, and building relationships in advance. They emphasized tracking laundering pathways over crime statistics, highlighting that understanding fund flows matters more than measuring amounts stolen.
So, let’s dive in.
Is the annual amount of crypto crime still relevant?
Nick started the discussion by suggesting that simply counting the number of crypto hacks and scams annually might not be the way of the future. He cited the February 2025 ByBit Exchange hack as an example, when the infamous Lazarus Group stole $1.5B in under 15 minutes. He also noted that since Crystal started recording such annual data in 2011, an astonishing $21,3B has been stolen in just over 1,000 known incidents, with 2022 ($4.2B) being the deadliest.
The panelists debated whether knowing aggregate losses continues to help. Nick argued that while the statistics indicate trends, their practical value is limited because unreported fraud leaves huge gaps in the data. Andrii commented that identifying trends remains helpful in informing law enforcement that crypto crime is growing, adding that the market seems unfazed by incidents like Bybit.
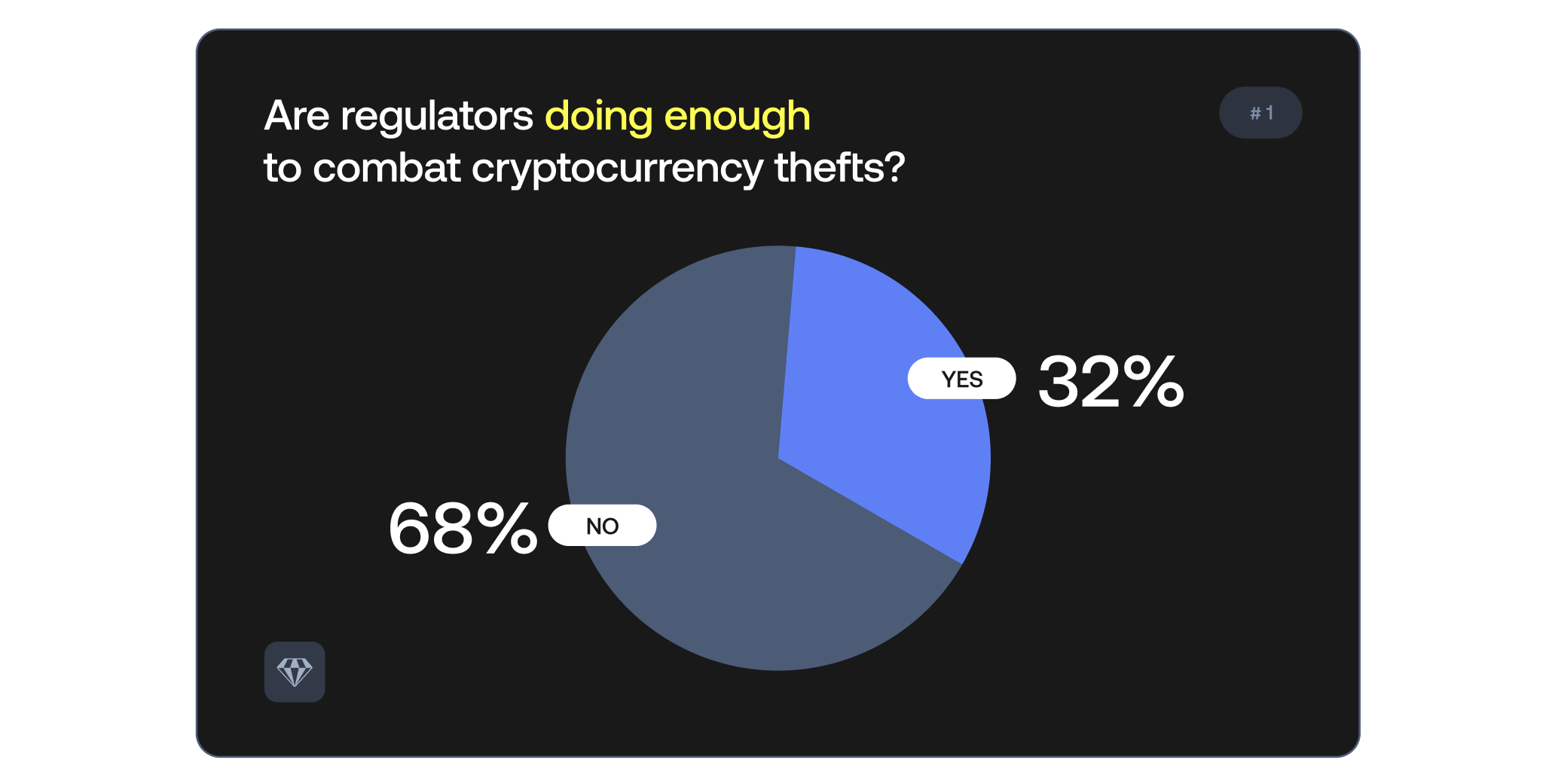
A full 68% of the audience believe that regulators are currently not doing enough to counter crypto thefts
A recurring theme was the lack of complete data, especially regarding fraud and recovery. Theft incidents are easier to count, but the numbers and amounts of fraud arelikely higher than what is known. Even when funds are stolen, the percentage recovered is tiny. Stolen assets tend to disappear quickly, and the industry lacks robust mechanisms to measure recovery.
So, while the statistics are striking, the real challenge lies in response capacity: how quickly exchanges, investigators, and regulators can act when a hack occurs.
Crypto crime trends and the rise of the Lazarus group
Crystal’s data shows that fraud and breaches dominate over 75–80% of cases. Attacks have shifted from multiple, minor hits to fewer, high-value strikes on major exchanges. Groups like the North Korea-linked Lazarus exemplify this. They inject malicious code and test systems, waiting for opportunities. Significant incidents like Bybit and breaches in JavaScript NPM libraries show that attackers prefer “bigger fish” targets for maximum payoff.
Andrii noted that Lazarus is non-specific in selecting victims, motivated by liquidity and opportunity—they will exploit any weakness but increasingly focus on high-value exchanges. However, he added that they likely planned the ByBithack up to a fortnight in advance.
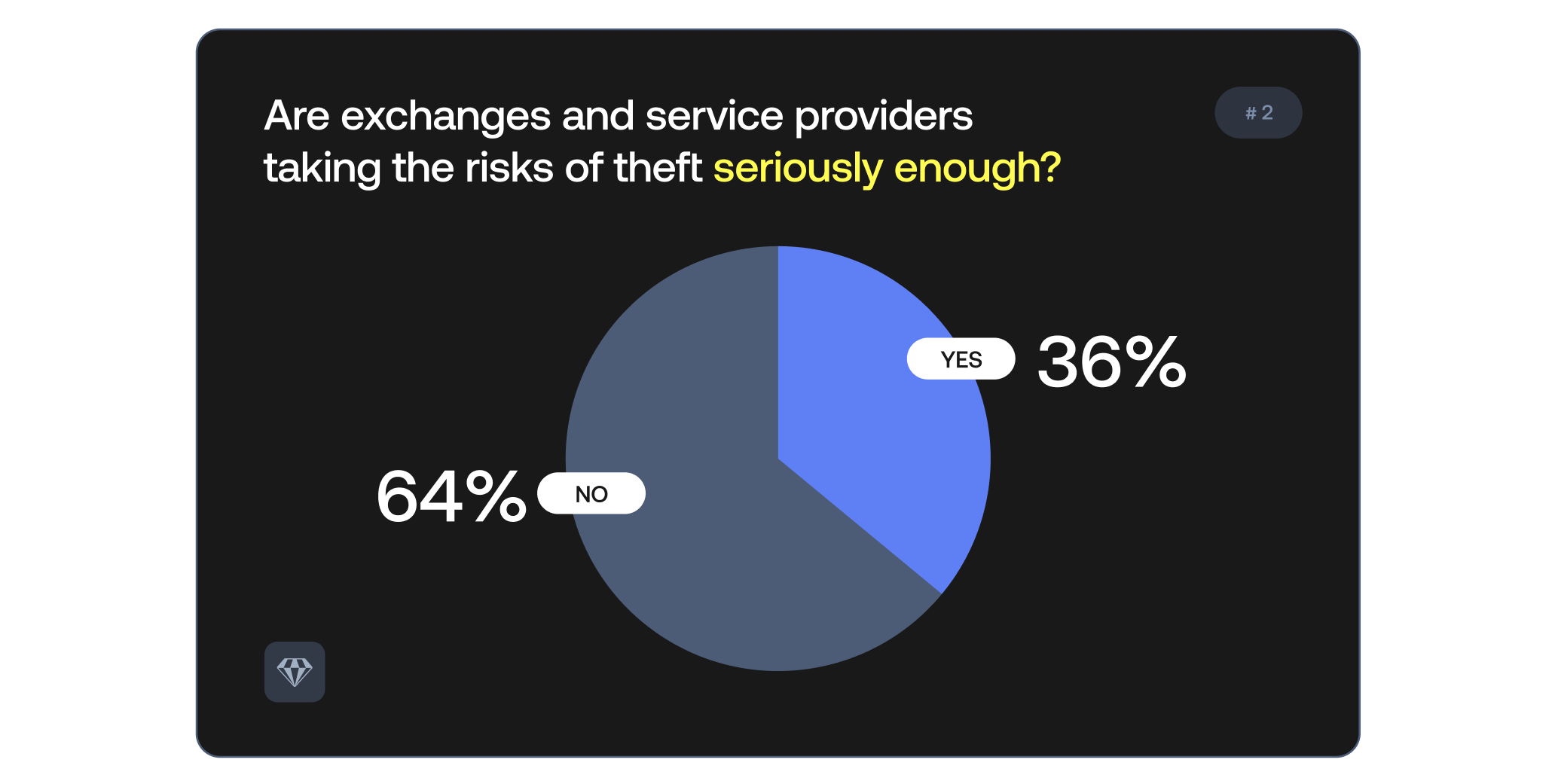
Similarly to the previous poll, 64% of the audience believes exchanges do not take the risks seriously enough.
He also pointed out that exchanges invest heavily in advanced security systems like multi-signature wallets and cold storage offline systems. However, attackers evolve their methods faster; even advanced defenses can fail against sophisticated operations. He stressed that improved security had little impact on the recovery of funds.
He also observed that the exchanges’ response to incidents had improved, citing how, in the Bybit case, the exchange openly communicated, launched public APIs for address blacklisting, and created a bounty program. This transparent communication strategy built trust, even if most funds were never recovered.
The industry has shifted towards a “crisis response” mindset that anticipates system failures, focusing on prevention, contingency, and communication. Nick partially attributed this to increased support from regulators.
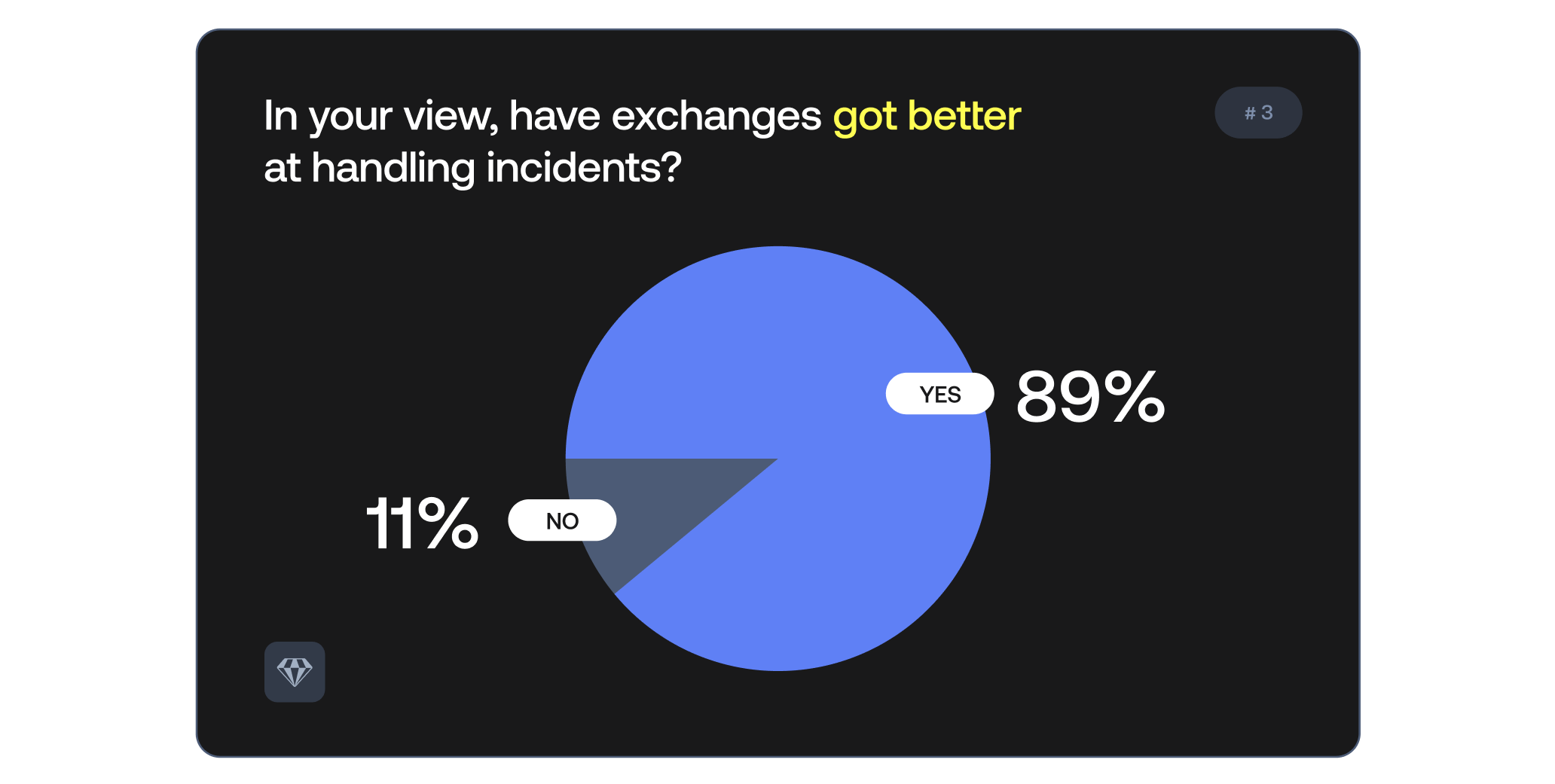
89% of respondents believe that exchanges’ ability to respond to incidents has improved over time.
One striking insight from Crystal’s research is that Friday sees the highest losses on aggregate. Andrii suggested that hackers exploit reduced security staffing and delayed responses at the end of the workweek. Lazarus often operates on Fridays to maximize the delay in detection and reaction. This trend emphasizes that exchanges must maintain full-scale security operations even during weekends and holidays, not just standard hours.
The role of law enforcement in combating crypto crime
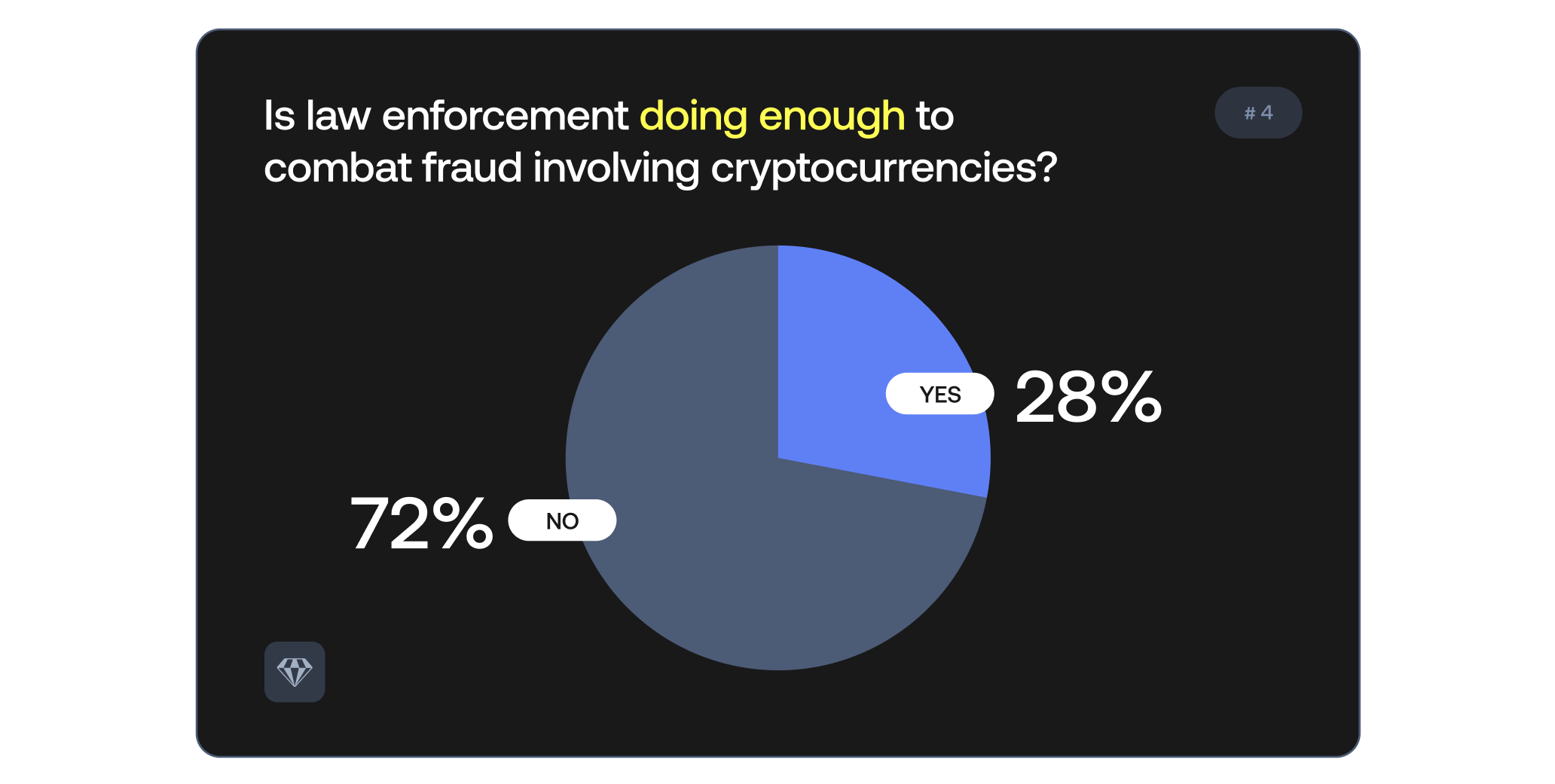
An overwhelming 72% of respondents believe law enforcement is not doing enough to combat crypto crime.
Andrii’s experience showed mixed results: some officers are highly skilled, but many lack a technical understanding of DeFi and tracing. Investigations often stall due to knowledge gaps, and he suggested better educating law enforcement on crypto currencies. Law enforcement’s response times also clash with crypto’s speed. Stolen assets can be laundered within seconds, but law enforcement processes take days. Nick agreed, adding that some victims are also unsure what information to pass on to law enforcement.
Regulation, cooperation, and exchange obligations to combat crypto crime
The discussion moved on to whether regulators should force exchanges to cooperate more with international investigations. While regulation can streamline processes, Andrii noted that current systems are slow and opaque, often taking days to freeze accounts while funds move in minutes. Exchanges and investigators should build relationships with regulators and law enforcement before crises occur, ensuring faster, better-informed responses.
The solution lies in preparedness: exchanges and service providers must establish pre-arranged protocols, legal contacts, and dedicated teams for emergencies, as well as build relationships with law enforcement agencies. Improving public-private partnerships is vital, as response speed against crypto crime is of the essence.
Money laundering tactics and evolving trends in crypto crime
After briefly discussing the attack vectors criminals favor, the discussion moved on to how attackers launder stolen crypto.
Key points:
- Decline of the use of mixers: With mixers more visible to authorities, criminals now prefer illegal services which can includebridges, DeFi protocols, and OTC services that lack strict KYC.
- Use of nested services: Criminals exploit legitimate exchanges indirectly through OTC desks, making tracing difficult.
- Marketing of illicit services: Andrii reported seeing ads on social media offering anonymous cash-outs in Europe, highlighting the normalization of laundering.
Nick observed that, overall, attackers pursue the path of least resistance when laundering their stolen crypto, avoiding visible mixers and preferring low-KYC services. DeFi protocols and meme coins represent another vector. While many are legitimate, their low barriers to entry attract fraudsters and rug-pull schemes.
DeFi, Meme coins, and regulatory risks
Nick emphasized that DeFi platforms must embrace responsible compliance if they want long-term business viability. Otherwise, they risk being stigmatized as havens for criminal activity, losing legitimate users, and inviting regulatory scrutiny. The discussion tied this to existential threats: regulators may intervene if your platform becomes synonymous with laundering or scams, and consumers will flee.
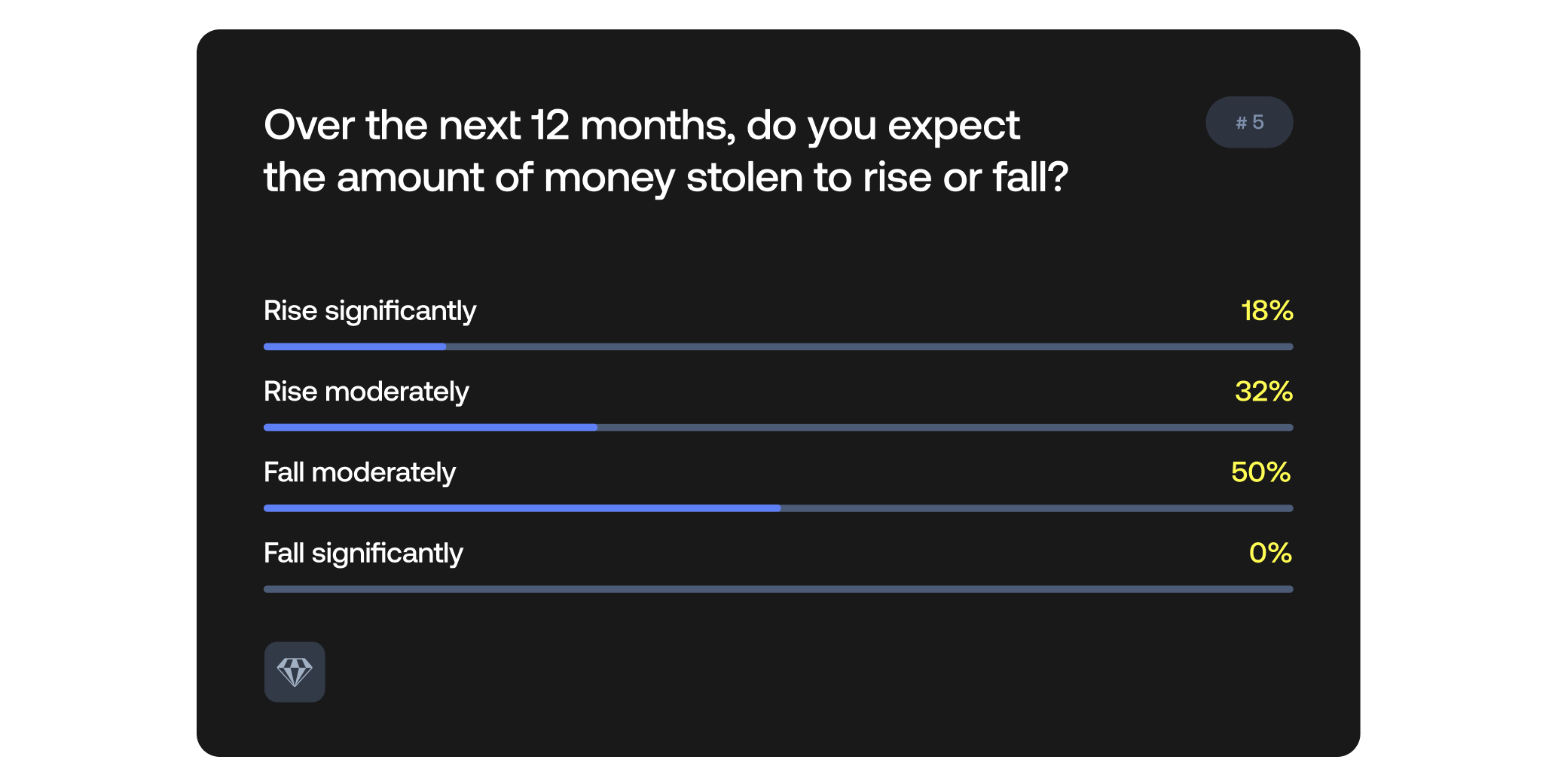
68% of the audience predict that crypto crime will increase over the next 12 months.
Andrii explained that several factors could drive increases or decreases in crypto crime, such as the ByBit heist, but rising crypto adoption rates will likely lead to more perpetrators and victims entering the market. Nick felt that a rise or fall in the amount of crypto crime in the next twelve months will demonstrate what crypto industry participants have learnt about improving their security.
Fraud, social engineering, and human weakness in crypto crime
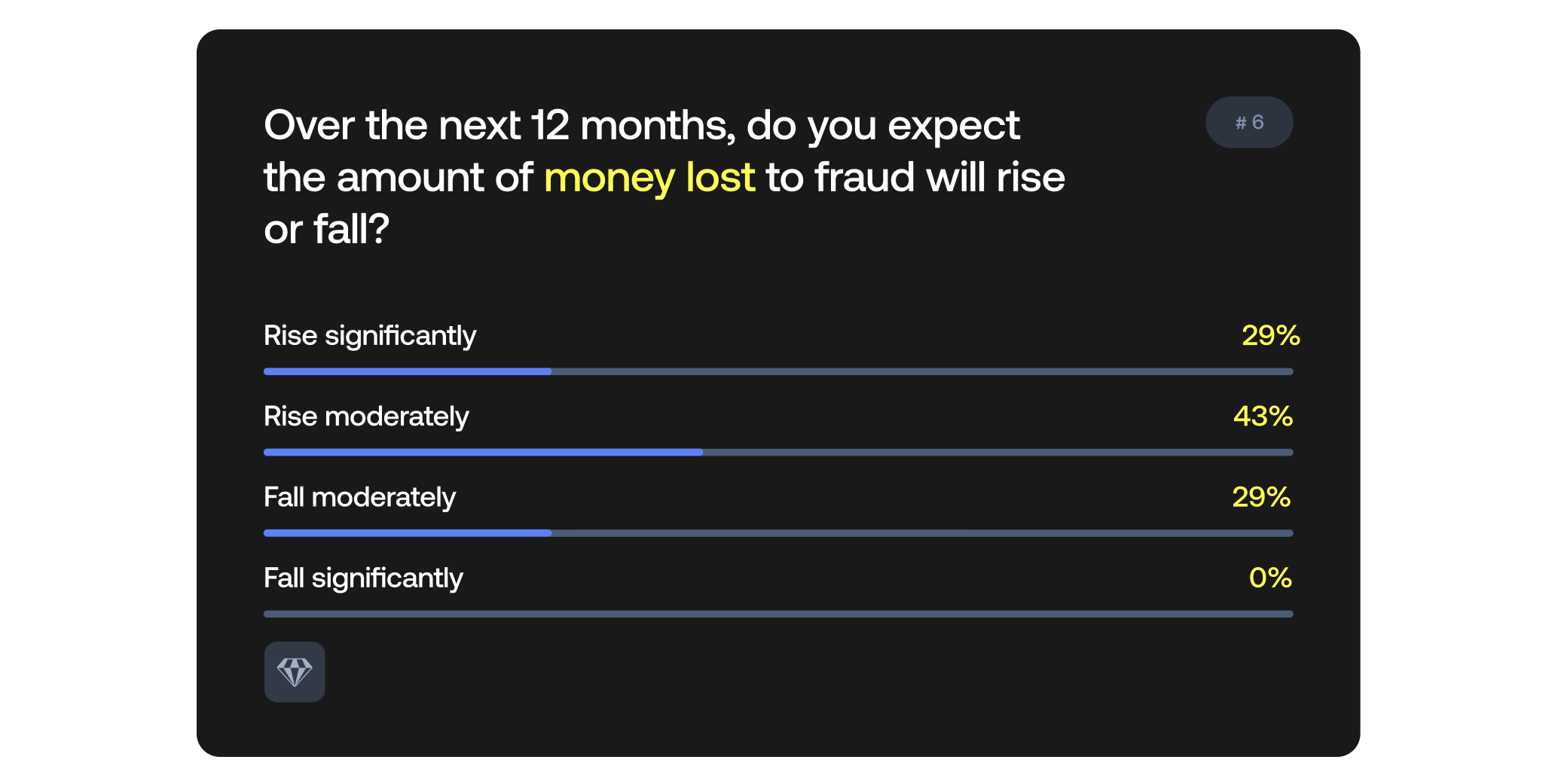
72% of respondents believe that the amount of money lost to fraud will increase in the next 12 months.
Drivers include lack of education, widespread scams, and the sophistication of social engineering. The key question is whether the industry has learned lessons from past hacks—custody practices, wallet management, and incident responses. Without systemic improvements, losses will keep growing. Nick and Andrii concluded that improved crypto user education and regulation will be needed to make fraud drop over the next 12 months.
The discussion then moved on to the rising sophistication of social engineering, including collecting victims’ data. Andrii described major SIM-swapping and impersonation scams, including one in August involving 780 BTC and another in April with 3,500 BTC. These scams use layered deception, fake support calls, and psychological manipulation to trick victims. Such incidents illustrate that while technological defenses advance, human vulnerability remains a major attack vector.
What single action will work best to disrupt crypto crime in the next twelve months?
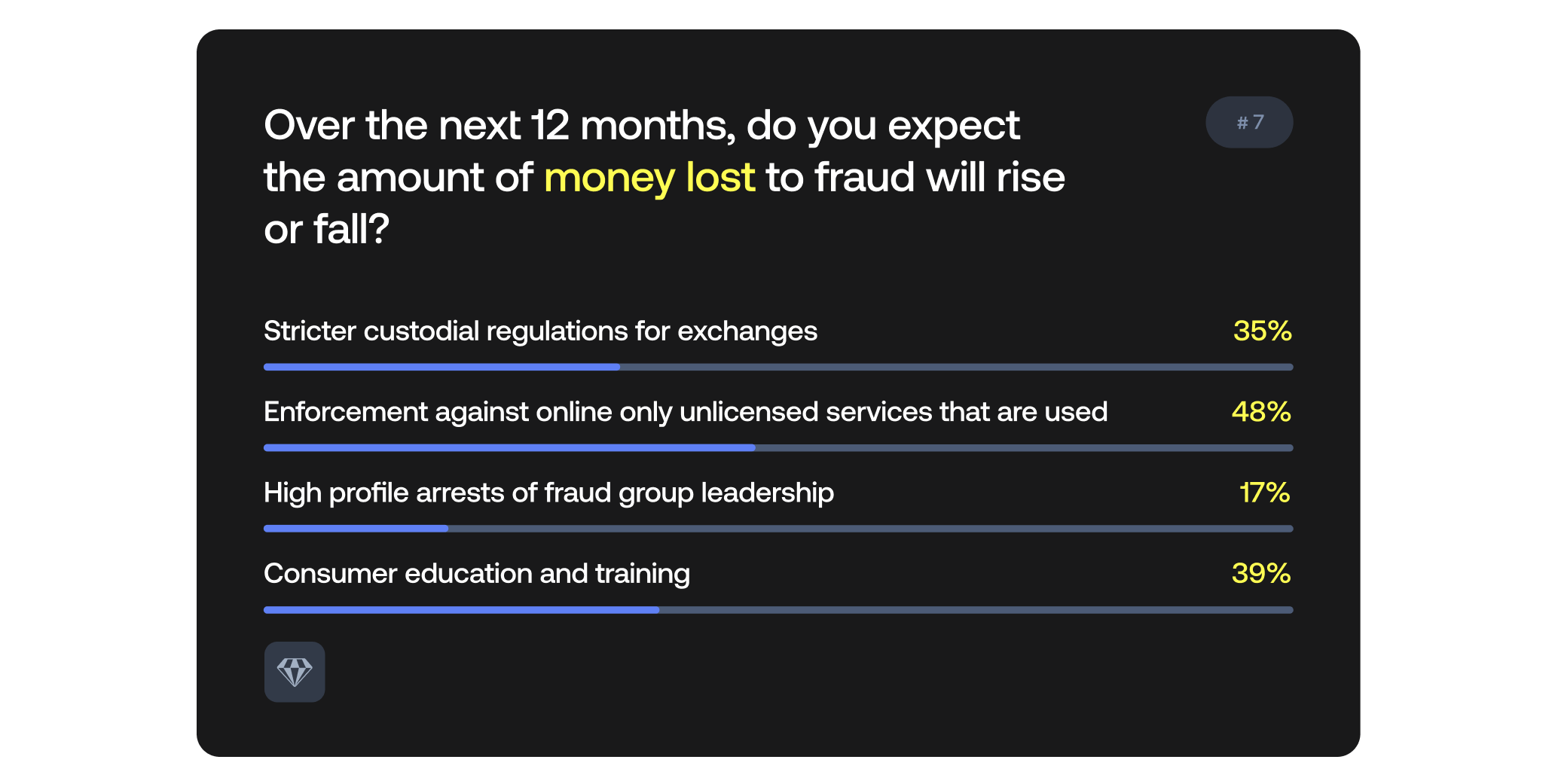
48% of the audience believe that enforcement against online only services will be the most effective.
Andrii chose regulation as the most important single disruptor of crypto theft until law enforcement can catch up. Nick chose enforcement, since although regulations set rules, grey-market services don’t care. While education and high-profile arrests might help, they cannot address systemic enablers.
Conclusions on the future of fighting crypto crime
Nick closed the webinar by saying that statistics on crypto crime, while useful in measuring the health of the industry’s growth, now matter less than understanding the mechanics of money laundering. Instead of focusing on how much is stolen and how many incidents there are, the priority should be mapping where stolen funds go, through which services, and how they re-enter the financial system.
He concluded by saying that the Bybit hack showed that cooperation, transparency, and readiness can mitigate crises, but without systemic change, criminals will continue exploiting the weakest links in the ecosystem. He then invited listeners to contact Crystal to discuss their current and future systems.
Watch the webinar below, and download the full 2025 crypto hacks & scams report here.



